A container arrives with its high-security seal perfectly intact, yet thousands of dollars in assets are gone. The security protocol didn't just fail; it was turned into a weapon. It was used to create a shield, a perfect illusion of safety that masked the crime.
The most dangerous vulnerability in your supply chain might not be a weak lock or a corrupt driver. It is the box of spare security seals sitting uncontrolled in your own facility. This is not a minor inventory issue; it is the source of a "perfect crime" toolkit you are providing to your internal adversaries.

Your insight is the absolute crux of the matter, and it's a lesson companies often learn after a devastating loss. The risk is not the cost of the lost seals. The risk is the capability an unlogged seal provides. It grants a dishonest employee the power to manufacture a false reality. I once investigated a recurring theft of pharmaceuticals. For months, the evidence was baffling. Every shipment departed with seal #A and arrived with seal #B, perfectly intact. The transport company was the prime suspect. The truth was an internal manager with access to an open box of seals. He was creating the perfect alibi for himself, using the company's own security tools as his shield.
What Defines an 'Uncontrolled' Security Seal Inventory?
Imagine a book of blank, signed checks left on a breakroom table. Or a company's official seal stamp available for anyone to use. This is precisely the nature of an uncontrolled security seal inventory. It is a catastrophic failure of internal control.
An inventory is "uncontrolled" the moment a security seal—a unique, single-use security credential—is not treated with the same reverence as a financial instrument. It is defined by open access, the absence of an issuance log, and a culture that views these critical assets as mere supplies.

The failure here is conceptual. When you see a box of 1,000 seals, you are not looking at a bulk commodity. You are looking at 1,000 single-use passwords for your physical assets. By leaving them uncontrolled, you are essentially publishing your password list. You are handing over the keys to the kingdom and inviting insiders to betray your trust without leaving a trace. Every unlogged seal is a pre-signed permission slip for fraud.
From Asset to Liability: It's About Process, Not Product
The line between a security asset and a liability is defined entirely by your process.
| Controlled Inventory | Uncontrolled Inventory (The "Blank Checkbook") |
|---|---|
| Storage: Seals in a locked cabinet, access restricted. | Storage: Seals in open boxes on accessible shelves. |
| Access: Only trained, authorized personnel can issue a seal. | Access: Any employee can grab a seal at any time. |
| Issuance: Every seal is logged out against a person and shipment number. | Issuance: No log exists. Accountability is zero. |
| Auditing: Regular physical counts are reconciled against the log. | Auditing: Discrepancies are impossible to find. Lost seals are invisible. |
If your process resembles the right column, your security seals are not protecting you; they are actively endangering your organization.
How Can Employees Exploit Spare Security Seals for Theft or Misuse?
For the opportunistic employee, your uncontrolled inventory isn't just a convenience; it is the cornerstone of a foolproof plan. It empowers them to execute a theft and then meticulously erase their own footsteps, leaving behind a fabricated trail of evidence.
The method is brutally effective. An insider breaks the officially logged seal to commit a theft or other unauthorized action. Then, they simply apply a fresh, unrecorded seal from the "shadow inventory." The container now appears secure. The crime is perfectly concealed behind a new layer of perceived integrity.
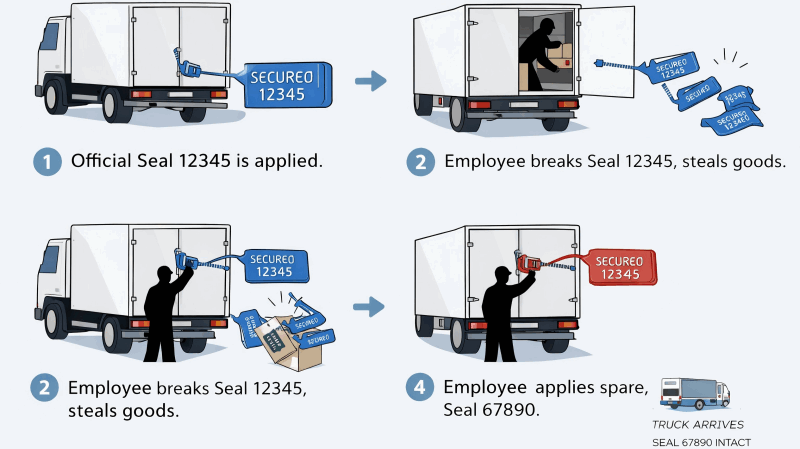
This is the "shield of false security" in action. I worked with a client whose fuel costs were inexplicably high. The cause was a driver using spare seals to run his own delivery business on the side. He'd break the official seal on his empty return trips, load a private shipment, then apply a new seal before returning to base. The cargo logs were clean, but the thousands of dollars in lost fuel and vehicle wear were bleeding the company dry. The unlocked box of seals was the tool that made his fraud possible.
The Criminal's Two Greatest Weapons, Provided by You
- The Shield of Concealment: The crime is hidden behind the powerful illusion of an intact seal. This delays detection, often for weeks or months, by which point the evidence is cold and the financial damage has compounded.
- The Sword of Deflection: By replacing the seal, the employee severs the Chain of Custody at its origin. When the loss is finally discovered, the investigation naturally focuses downstream, on the transport route or receiving end. The insider remains above suspicion.
Your negligence becomes their greatest asset.
Why Inaccurate Seal Records Can Invalidate Your Entire Security Protocol?
A security protocol is a promise backed by data. When that data is flawed—when the seal number in the log does not match the seal on the container—the promise is broken. The entire system collapses into a worthless ritual.
Inaccurate or non-existent records render the unique serial number—the heart and soul of a security seal's function—utterly meaningless. The physical seal becomes an empty symbol, its integrity nullified by the failure of the process meant to support it. Your investment in high-strength materials and anti-spin features is wasted.

Here is the brutal financial truth: in a legal or insurance dispute, your security seal log is your primary evidence. If you present logs that are inconsistent, incomplete, or proven to be unreliable because of an uncontrolled inventory, you have effectively admitted your own negligence. An insurance company has every right to deny your claim. They will argue you cannot prove where or when the loss occurred. Your failure to control your inventory now has a real, and often massive, price tag. Your risk management strategy is built on a foundation of sand.
The Domino Effect of a Failed Process
- The Audit Trail Shatters: An unbroken chain of data is the only thing that gives a seal its power. A wrong number destroys it.
- Accountability Evaporates: Without reliable data, no one can be held responsible. It fosters a culture of carelessness.
- Security Becomes Theater: Your team goes through the motions of a security process that they know has no real teeth.
- Financial Recourse is Lost: Insurance claims are denied. Legal disputes are lost. You bear the full cost of the theft.
Your process is either your strongest defense or your most glaring weakness. There is no middle ground.
Beyond Financial Loss: The Impact on Your Company's Reputation and Trust
The theft of goods is a quantifiable loss. The destruction of trust is not. When a customer, partner, or insurer discovers your internal controls are a sham, the reputational damage can cripple your business for years.
Every security incident enabled by your own poor processes broadcasts a message of incompetence. It tells your customers you cannot be trusted with their business. It tells your logistics partners you are a high-risk liability. It tells your own honest employees that their integrity is not valued.

I saw a thriving food exporter almost wiped out by this. A shipment arrived contaminated, with a replaced seal. The immediate loss was $50,000. The real damage was their largest client, a global supermarket, immediately suspending their multimillion-dollar contract. The client's logic was simple: "If you cannot control a simple box of seals, how can we trust you to control the safety of the food you provide us?" The loss of trust was infinitely more costly than the loss of product.
The Lingering Poison of a Damaged Reputation
- Customer Exodus: Clients will leave for competitors who can demonstrate robust security and professionalism.
- Partner Distrust: Your supply chain partners may enforce costly extra checks or simply refuse to work with you.
- Soaring Insurance Costs: Your risk profile skyrockets, and your premiums will reflect that.
- Internal Decay: Honest employees lose morale, while a culture of impunity emboldens further wrongdoing.
Trust is the currency of business. An uncontrolled seal inventory is a bonfire waiting to burn it all down.
Establishing a Chain of Custody: Your First Line of Defense
The solution is not about expensive technology. It is about reclaiming control through unwavering discipline. You must establish a strict Chain of Custody for your security seals, treating each one as the accountable, single-use security credential it is.
This is your most powerful defense. It starts the moment a new box of seals arrives and ends only when a used seal is confirmed destroyed after its journey. It means every seal is logged, secured, and signed for by an accountable individual. It requires you to stop seeing "a box of seals" and start seeing "an inventory of 1,000 unique keys."
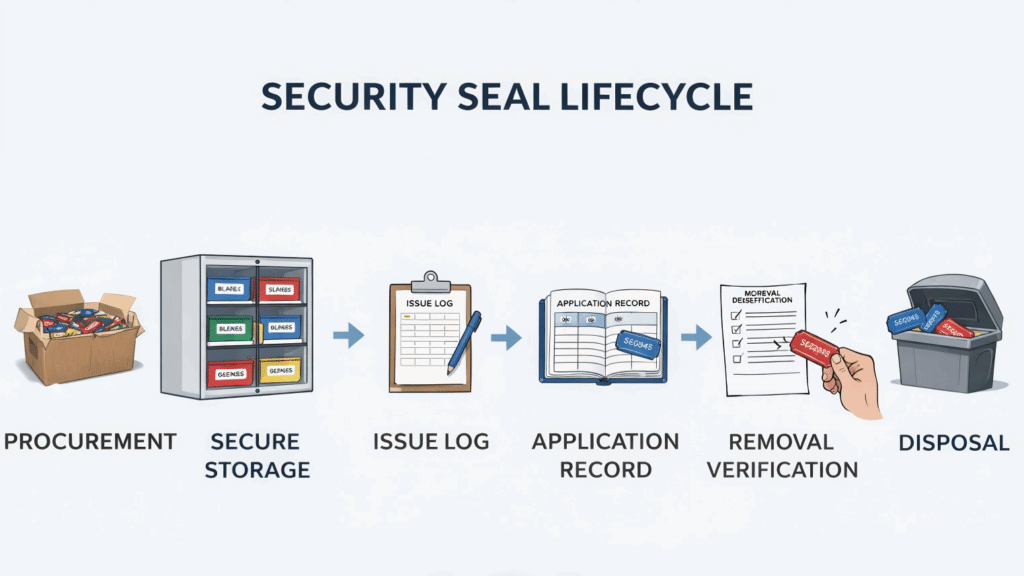
When we solved the problem for the pharmaceutical distributor, we didn't install a complex system. We implemented discipline:
- All seals were moved into a locked manager's office.
- A simple logbook was mandated: Date, Driver, Shipment ID, Seal # Issued, Signature.
- Dispatch papers were withheld until a seal was signed for.
This low-tech, high-discipline process immediately eliminated the vulnerability. It was about owning the process, not just the product.
The 4 Pillars of an Impenetrable Seal Chain of Custody
- Secure Storage: Seals are stored as you would store cash or checks—under lock and key, with restricted access.
- Logged Issuance: No seal ever "walks away." It is formally issued and logged against a person, creating an unbreakable link of accountability.
- Mandatory Reconciliation: The seal number issued MUST match the number verified upon arrival. Any mismatch is a red-alert security event, not a clerical error.
- Rigorous Audits: A physical count of your seal inventory against your logbook is non-negotiable. This is how you find leaks before they become floods.
This discipline is not optional; it is fundamental.
Conclusion
An uncontrolled seal inventory is a ticking time bomb. It silently offers your greatest internal threats a shield to hide behind. Reclaim control by establishing a rigorous Chain of Custody, and you will disarm this hidden threat for good.
Forge a True Chain of Custody with ProtegoSeal
A security protocol is only as strong as its weakest link. At ProtegoSeal, we understand that true security comes from a combination of world-class products and ironclad processes. Contact us to move beyond security theater and build a resilient Chain of Custody that protects your assets and your reputation.