Confused by hologram security features? Choosing wrong means wasted money or a false sense of protection. Real security comes from understanding the layers of defense, from basic visual deterrents to advanced forensic markers.
The security of a hologram label is defined by layers of features, from overt visual effects anyone can see, to covert elements for inspectors, and unique forensic markers for legal verification. A truly secure hologram integrates these features into a unified, multi-layered defense system.
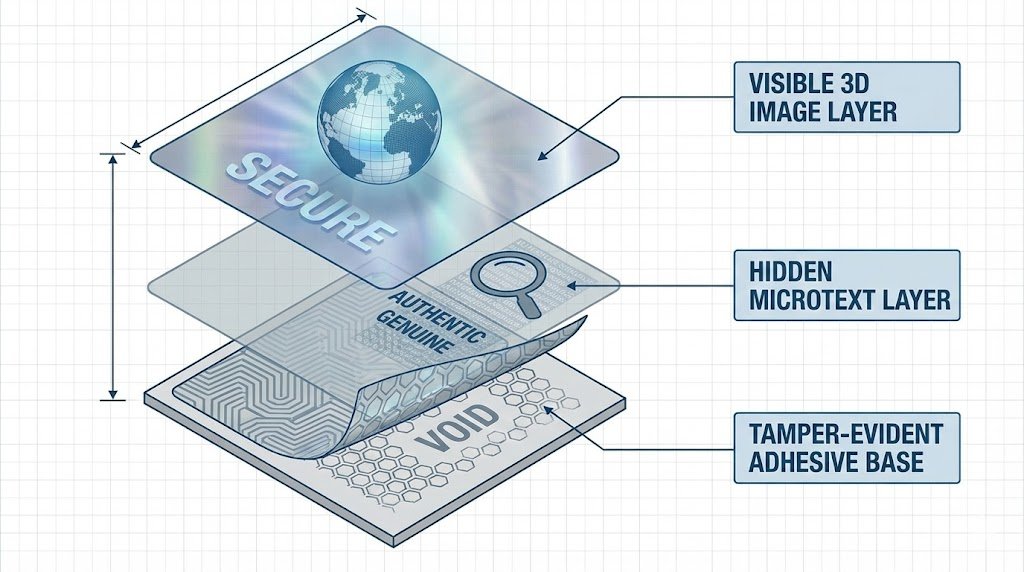
The security of a hologram isn't determined by a single technology, but by how multiple technologies form a "multi-layered, interlocked verification system." I architect security solutions based on three tiers of verification. Tier 1 is for the public, using the naked eye. Tier 2 is for channel inspectors using simple tools. Tier 3 is for brand owners, using lab equipment for forensic and legal proof. A label's real strength comes from its defensive depth across these three tiers. Let's break down that system.
The Foundational Layer: Overt Visuals in Hologram Labels
This is the first and most visible line of defense. If counterfeiters can't even get this part right, their fakes are easily spotted, empowering your customers to protect themselves and your brand.
Overt features are the security elements that can be verified by the public with the naked eye, without any special tools. They are designed to be intuitive and immediately distinguishable from a flat, printed imitation. According to the ISO 12931 standard for authentication solutions, visible features must be easily recognizable by the lay public to be effective.

This is your Tier 1: Public Verification level. Its purpose is to make authentication easy for the end-user. While a determined professional might replicate some of these effects, casual counterfeiters using simple printing methods cannot. The goal is to create visual effects that are impossible to create with ink on paper. I once had a client in the electronics space who was battling fakes that looked identical in the packaging. By adding a simple 3D hologram with a clear parallax effect, their customer service calls about fakes dropped by 70%. They had successfully deputized their entire customer base as brand protectors.
Key Overt Features (Tier 1)
| Feature | Description | How to Verify |
|---|---|---|
| 2D/3D Depth & Parallax | The image has multiple layers; a foreground and a background. | Tilt the label. The foreground should appear to float above the background. |
| Kinetic Effects | Patterns (like guilloché lines) or text seem to animate or move. | As you rock the label, the patterns should shimmer, expand, or rotate. |
| True Color Images | The hologram displays a specific, true-to-life color image at a certain angle. | Tilt the label until you see the full-color, photo-realistic image appear clearly. |
The Next Level: How Tamper-Evident Features Secure Your Hologram Labels
What if counterfeiters don't copy your hologram, but just move a real one? A perfect hologram on a fake product is a security failure. This is where the label's construction becomes critical.
Tamper-evident features are built into the material of the hologram label itself. They provide irreversible proof if someone attempts to remove the label and transfer it to another product, destroying the label in the process.

This is a crucial feature that spans both Tier 1 (Public) and Tier 2 (Inspector) verification. Anyone can see that a label has been tampered with if it's broken or leaves a pattern. This addresses the critical threat of "transference." A secure hologram must be a permanent fixture, not a removable accessory. It must create an inseparable bond with the product it is protecting. I always insist that the adhesive and material science behind the label are just as important as the optical science of the hologram itself, complying with rigorous ASTM testing standards for pressure-sensitive adhesives. A beautiful image on a cheap, peelable backing is not a security feature; it's a liability waiting to be exploited.
Common Tamper-Evident Technologies
- Frangible/Destructible Material: The label is made from an ultra-brittle material that shatters into tiny pieces upon any removal attempt.
- Pattern Release: When peeled, the tamper evident label leaves behind a pattern (e.g., "VOID," "OPENED," checkers) on the surface, and the label itself is damaged.
- Selective Release: A portion of the hologram's metallic layer is left behind, permanently scarring the image.
Advanced Security: Uncovering Covert Features Hidden in Hologram Labels
Your public-facing features deter amateurs. But for professionals in your supply chain—distributors, customs agents, and inspectors—you need a verification method that is quick, reliable, and invisible to counterfeiters.
Covert features are security elements hidden within the hologram that are invisible to the naked eye. They require a simple tool, like a magnifying glass or a specific light source, to be revealed.

This is the core of Tier 2: Channel Inspector Verification. These features are your secret handshake. Because counterfeiters don't know they exist, they don't bother trying to copy them. This allows your team to quickly and definitively separate genuine products from fakes without needing a lab. In a project for a pharmaceutical client, we embedded a UV logo that was only visible under a 365nm blacklight. Their customs brokers were equipped with simple UV keychains. This allowed them to verify entire pallets in minutes, creating a powerful security checkpoint that was completely invisible to the public and counterfeiters.
Key Covert Features (Tier 2)
- Microtext/Nanotext: Text so small it appears as a solid line to the naked eye. Verifiable with a magnifying glass or microscope.
- UV/IR Ink: Graphics or codes printed with ink that is invisible in normal light but glows under Ultraviolet (UV) or Infrared (IR) light.
- Laser-Readable Images: A hidden image that is only visible when illuminated by a laser of a specific frequency.
Expert-Level Protection: Why Serialized Hologram Labels Are Unbeatable
Generic holograms protect your product type. Serialized holograms protect each individual item. This creates a powerful link between the physical product and its digital record.
Serialization means every single hologram label is printed with a unique, traceable number or code. This "one item, one code" approach turns each label into a unique fingerprint, enabling track-and-trace capabilities and digital verification.

Serialization elevates your security into Tier 3: Forensic & Digital Verification. While an inspector can check the number (Tier 2), its real power is in the backend database. This unique identifier provides a definitive record of the product's authenticity, manufacturing date, and intended destination. For a high-value software client, we implemented serialized QR code holograms tied to their activation database. If a customer called with a key from a non-serialized hologram, the support team knew it was a pirated copy instantly. This not only protected revenue but also provided invaluable data on where the pirated copies were originating. Serialization creates an irrefutable audit trail for every single item, which is essential for legal disputes and high-stakes investigations.
The Ultimate Security: How Origination Defines a Hologram Label's Integrity
All the features in the world are useless if they can be copied. The ultimate security of a hologram lies in the complexity and proprietary nature of its creation—the master origination.
Hologram origination is the highly technical process of creating the master plate from which all holograms are replicated. The security and integrity of a hologram are determined by the sophistication of this master, which can involve techniques like electron-beam lithography that are beyond the reach of counterfeiters.

This is the foundation of your entire Tier 3: Forensic Verification system. While you can't see the origination technique just by looking at the label, a forensics lab can. They can analyze the microscopic structures—the grating patterns, the dot-matrix layout, the specific angles of refraction—and compare them against a known genuine sample. This is the holographic equivalent of DNA. A counterfeiter might mimic the look, but they cannot replicate the unique "genetic code" of a high-security master. When I work with clients on projects where the stakes are incredibly high (like government documents or high-end luxury goods), the investment in a proprietary, custom hologram design is non-negotiable. It's the ultimate guarantee of authenticity.
Conclusion
A hologram's strength is not in a single feature, but in its integrated, multi-layered system of defense. This tiered approach ensures security at every level, from the consumer to the courtroom.
Build Your Defense in Depth with ProtegoSeal
Understanding these layers is the first step. Implementing them is the next. At ProtegoSeal, we design and manufacture hologram labels with a strategic, multi-tiered approach to security. Contact us to build the interlocked verification system your brand deserves.