You've invested in high-security seals, but inventory still vanishes and shipments arrive with questionable integrity. You're stuck in a cycle of investigations that lead nowhere, causing frustration and significant financial losses. The painful truth is that the best seal in the world is useless without a bulletproof process behind it.
A security seal management program is a complete system of procedures for controlling, issuing, tracking, verifying, and auditing every security seal in your operation. It transforms seals from simple locks into critical data points within a controlled process, ensuring undeniable accountability from start to finish.
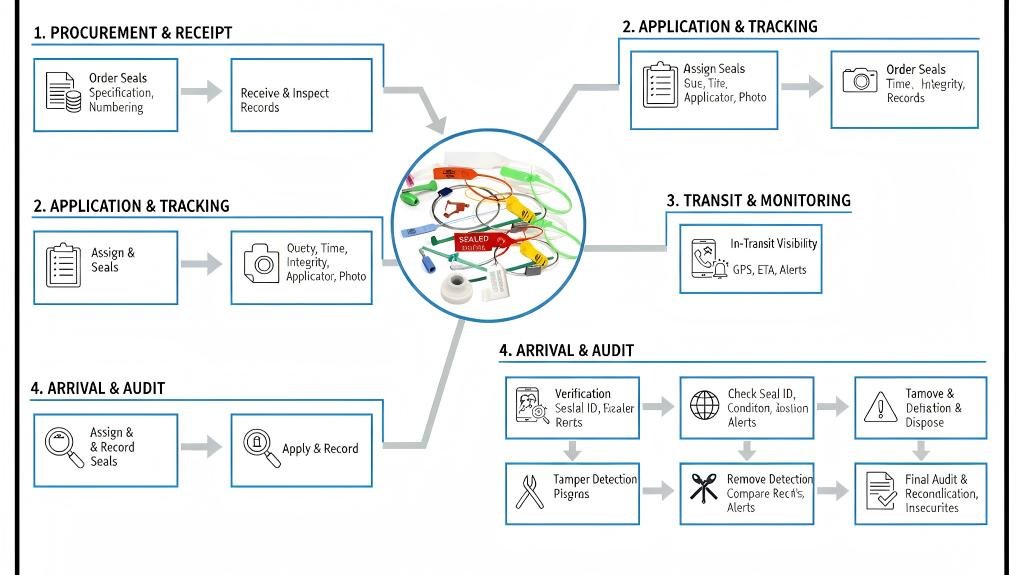
I learned this the hard way on a project years ago. A client was using our best bullet seals but still had inventory go missing. After a deep dive, we found the problem wasn't in transit; it was in their own warehouse. Seals were stored in an unlocked desk drawer, and anyone could grab one. The issue wasn't the seal's strength but the weakness of the human process. This is when I truly understood your insight: the program's strength comes from creating "interlocking mechanisms," where each step of the process automatically checks the previous one.
Where to Start? Mapping Your Key Security Seal Application Points
Starting a program from scratch feels overwhelming. The common mistake is to just write a rule: "All trailers must be sealed." This is too vague and leaves dangerous gaps.
The first, essential step is to physically map every single point in your operation where a seal should be applied. These are your Seal Control Points (SCPs). This map provides the foundation for your entire program, leaving no ambiguity about where and why a seal is used.

Creating this map is the first "interlocking" step. It defines the official playing field. If a seal shows up on a manifests but the location isn't a designated SCP, it immediately raises a red flag. This process forces you to think critically about your entire supply chain, from raw materials leaving a supplier to finished goods arriving at a customer. I guide clients through this by having them walk their own factory floor, asking at every door and every stage: "If this were breached, how would we know?" That question builds your map.
Identifying Your Seal Control Points (SCPs)
| SCP Location | Associated Risk | Recommended Seal Type | Reason for Sealing |
|---|---|---|---|
| Outbound Shipping Containers | High (International transit, theft, smuggling) | High-Security Bolt Seal | ISO 17712 Compliance, Proof of Integrity |
| Domestic Trailer Doors | Medium (Theft during transit) | Cable Seal or Plastic Truck Seal | Tamper Evidence & Access Record |
| High-Value Inventory Cages | Medium (Internal theft) | Fixed-Length Plastic Seal | Access Control & Audit Trail |
| Emergency First-Aid Kits | Low (Ensuring contents are complete) | Pull-Tight Seal | Tamper Evidence |
How to Implement Full-Lifecycle Traceability for Every Security Seal?
You've mapped your data points, but your seals are still just loose items in a box. A missing seal is a major security risk. Treat every seal like a critical asset by managing its entire lifecycle.
Establish a full traceability system to track each seal from the moment you receive it to its final disposal. This means logging when seals are received, storing them securely, and requiring staff to officially sign them out before use. This creates an unbroken Chain of Custody for your inventory.
Security Seal Lifecycle Management
A seal cannot be applied unless it was officially issued. A driver cannot just grab one. This process turns a lost seal from a minor inconvenience into a traceable security event.
| Stage | Action Required | Why It's Critical |
|---|---|---|
| 1. Procurement | Log all incoming seal numbers from your supplier. | Establishes the official start of your asset inventory. |
| 2. Secure Storage | Store all seals in a locked, controlled area. | Prevents unauthorized access and theft of unused seals. |
| 3. Issuance | Staff must sign out specific numbered seals from a manager. | Creates personal accountability. A missing seal is now a logged event. |
| 4. Application | The assigned person applies the seal to the asset and logs it. | Connects the specific, issued seal to a specific shipment. |
| 5. Verification | The seal is inspected and its removal is logged at the destination. | Confirms the seal completed its intended journey securely. |
| 6. Disposal | Destroy the seal completely after removal (e.g., cutting a bolt seal). | Prevents fraudulent re-use of a legitimate seal number. |
Crafting the SOP: Security Seal Application, Recording, and Inspection
Having a map and a log is great, but inconsistent actions by your team can still break the chain. How do you ensure everyone performs these critical tasks the same way, every time?
You need a clear, concise Standard Operating Procedure (SOP). This document is a simple, step-by-step guide that details exactly how to apply a seal, where to record its number, and what to look for during inspection. Pictures and simple language are key.

A strong SOP is a training tool and an accountability contract. It should specify the "four-point check" for every application:
- Check the seal: Confirm it's the correct type from the log.
- Apply the seal: Follow the visual guide in the SOP.
- Tug the seal: Physically pull on it to confirm it's locked.
- Record the number: Immediately write the unique ID on the Bill of Lading or into the digital system.
This SOP acts as the next interlock. The person receiving the cargo uses their copy of the SOP for inspection. If the seal number doesn't match the manifest, or if it shows signs of tampering not documented, the SOP dictates that the "Breach Protocol" must be activated. This makes the receiver the natural auditor of the sender's work.
What Constitutes a Security Seal Breach and What Is Your Response Protocol?
A driver arrives and the seal number doesn't match the paperwork. What happens next? A panicked phone call? An argument? This chaotic response is a security failure in itself.
A breach is any deviation from the SOP. This includes a broken or missing seal, a mismatched number, or visible signs of tampering. Your response must be a pre-defined, unemotional protocol that outlines immediate actions, communication channels, and documentation requirements.

This protocol is arguably the most critical part of your entire program. It removes panic and replaces it with procedure. Your SOP should state clearly: "If the seal number does not match the manifest, DO NOT OPEN THE CONTAINER." The driver's job is not to solve the mystery; it is to document the facts and escalate. I worked with a client to create a simple report form on a mobile app. When a breach was detected, the driver had to take photos of the seal and the manifest and upload them before they could even call their manager. This captured pristine evidence before anyone could disturb the scene, providing an unshakeable foundation for any subsequent claim or investigation. This is a core practice of incident response.
Beyond the Logbook: Establishing a Robust Security Seal Auditing Process
Your program is running, but how do you know it's truly working? Relying on day-to-day operations to catch errors is not enough. You need to actively look for weaknesses.
A robust auditing process is the final, and most important, interlocking mechanism. It verifies the entire system. This involves regular, scheduled reviews of your seal logs and periodic, unannounced spot-checks of sealed assets to ensure the process outlined in your SOP is being followed to the letter.

This is the "Trust, but verify" stage. The audit closes the loop and makes the entire system self-aware and self-correcting. The audit isn't just about catching errors; it's about reinforcing the importance of the program. Your audit should answer key questions:
- Are all procured seals accounted for in the master log?
- Do the issuance logs match the numbers on shipping documents for a given period?
- During a spot check, does the physical seal on a trailer match the documentation perfectly?
- Are old breach reports properly filled out and resolved?
Finding a discrepancy isn't a failure; it's a success for the audit. It highlights a weakness you can now fix. This continuous improvement cycle is what transforms a good program into an ironclad one.
Conclusion
An ironclad security seal program isn't about buying expensive seals. It's about building an interlocking process of mapping, tracking, standardizing, and auditing that makes every person in the chain a natural guardian of your assets.
Build Your Interlocking Security Program with ProtegoSeal
Don't just buy seals; build a system. ProtegoSeal has over 15 years of experience helping clients design and implement robust security seal management programs. We offer not just the hardware, but the expertise to make it work. Contact us to schedule a consultation and fortify your supply chain.