A container arrives with a broken security seal, and your customer claims the goods are short. You know you sealed it correctly, but how do you prove it? Without a detailed record, you're left in a "he said, she said" battle that can cost you thousands in claims and erode client trust.
A security seal logbook is your single source of truth. It's a meticulously kept record that tracks every essential data point in a seal's life. This logbook creates an unbroken, legally defensible Chain of Custody, providing the undeniable evidence needed to protect your business.

The real power of this document hit me when a client faced a $50,000 claim for missing electronics. Their customer presented a photo of a cut bolt seal. It seemed like an open-and-shut case against my client. But they had followed our advice and kept a perfect logbook. They presented their records, showing exactly who sealed the container, when, and—most importantly—the documented check-in by the freight forwarder confirming the seal was intact upon collection. The claim was dropped. The logbook wasn't just a record; it was their legal shield.
Unique Security Seal Number: The Core of Your Tracking System
You receive a box of 1,000 security seals. If you don't track the numbers, they're just anonymous pieces of plastic. An unrecorded seal number offers zero traceability and zero accountability.
The unique, laser-engraved serial number is the heart of your entire security program. Recording this number is the first and most critical step in giving a seal its identity and making it a trackable asset.

Think of this number as the seal's social security number. It's the one piece of data that connects all other information. Every action—application, inspection, removal—will be tied back to this specific number. In our client's legal dispute, the first thing the lawyers asked for was the disputed seal number. Because my client had logged it, they could immediately pull up its entire history. Without that recorded number, their defense would have ended before it even started. It's the foundational link in your Chain of Custody.
Application Point & Asset ID: Answering the "Where"
Just knowing the seal number isn't enough. A log entry that says "Seal #1234567 applied" is useless. Where was it applied? On what asset?
You must record the specific application point (e.g., "Rear Door, Driver's Side") and the specific asset ID (e.g., "Trailer #T-802" or "Container #MSCU-681947"). This creates an unarguable link between the seal and the asset it was securing.

This step prevents disputes about which container was sealed. I've seen cases where a driver has multiple pickups and the paperwork gets mixed up. A logbook that clearly states "Seal #1234567 applied to Container #MSCU-681947" provides concrete evidence that closes this loop. It removes all ambiguity. For your Chain of Custody to be legally sound, it has to be specific. Vague information creates reasonable doubt, and reasonable doubt is where you lose claims.
Date and Time of Application: Establishing the Timeline
A seal was applied. That's a good start, but WHEN was it applied? Without a timestamp, you have a major gap in your evidence trail.
Recording the exact date and time of application is non-negotiable. This data point establishes the official start of the sealed journey and becomes a critical reference point for every subsequent event in the seal's life.
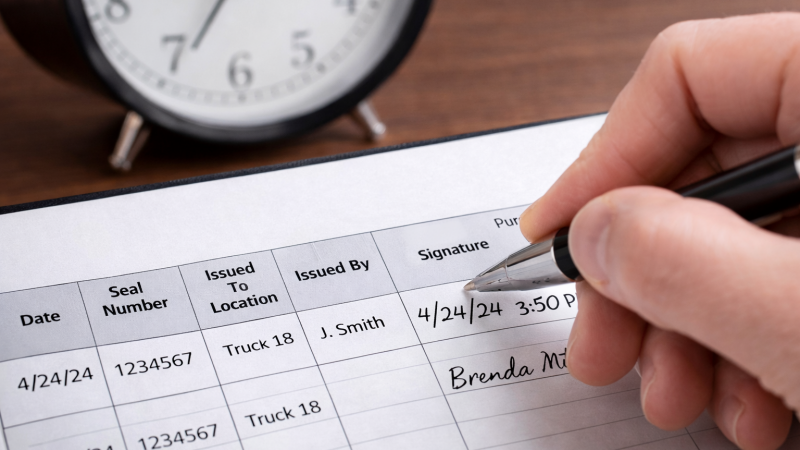
The timestamp is your anchor in reality. If a security camera at a port shows your container being tampered with at 3:00 PM on Tuesday, your logbook better show that the original seal was applied before that time. This data provides the temporal context that is essential for any investigation. It helps you reconstruct the sequence of events with precision, a core requirement for building a credible and admissible evidence trail. In a dispute, a timeline isn't just helpful; it is everything.
Name and Signature of Applicator: Ensuring Accountability
A seal was applied at a specific time and place. But who did it? An anonymous log entry weakens your entire process, making it easy for people to deny responsibility.
Every log entry for an application must include the printed name and signature of the person who physically applied the seal. This introduces personal accountability into the process, transforming it from a robotic task into a personal responsibility.
This is a powerful psychological tool. When an employee signs their name, they are personally vouching for the fact that the procedure was followed correctly. It’s no longer an abstract company policy; it's their own reputation on the line. I always tell my clients that this is the step that turns a passive process into an active one. In the event of an incident, you know exactly who to talk to. This isn't about placing blame; it's about efficient investigation and demonstrating to auditors and courts that you have a system of individual responsibility.
Security Seal Condition Upon Inspection: The Moment of Truth
Your sealed container arrives at its destination. The driver hands over the paperwork. How do you confirm that the security promised at the origin is the security you are receiving now?
The receiver must inspect the seal's condition before removing it and record their findings. This "moment of truth" either validates the entire journey or triggers a breach protocol. The inspection must be a documented step.

This is the interlocking mechanism in action—the receiver is auditing the sender's work. The logbook on the receiving end should have a space to confirm the seal number matches the manifest and to note the seal's condition.
Inspection Checklist:
- Number Match: Does the physical seal number exactly match the number on the manifest/Bill of Lading?
- Physical Integrity: Are there any signs of tampering (scratches, glue, cut marks, discoloration)?
- Tug Test: Is the seal firmly locked? (Give it a strong pull).
Recording a "Seal OK" is just as important as recording a breach. It officially transfers custody and confirms the integrity of the shipment up to that point.
Date and Time of Removal: Closing the Security Loop
The seal has been inspected and verified. Now it's time to open the container. Just cutting the seal and discarding it leaves the story unfinished.
You must record the exact date and time the seal was officially removed. This data point formally closes the security loop for that specific journey, defining a clear end to the period of secured transit.

Why is this so important? It protects you from claims of theft that occur after delivery. Imagine your container is delivered and the seal is cut. Two days later, the customer claims items are missing from their warehouse. Your logbook, showing the seal was intact upon arrival and cut at a specific time, proves the goods were secure while under your control. The liability officially transferred when that seal was cut. Without this final timestamp, the timeline remains open and ambiguous, leaving you vulnerable.
Name and Reason for Removal: Documenting the Final Step
The seal was cut at a specific time. Who cut it, and why? Was it the intended recipient for routine unloading, or was it a customs officer for a surprise inspection?
The final data point must be the name of the person who removed the seal and the reason for removal (e.g., "Routine Unloading," "Customs Inspection," "Damaged in Transit"). This entry provides the final piece of context for the entire journey.

This final step is crucial for completing your evidence file. If a customs agency breaks your seal, this record, often accompanied by official customs paperwork, proves why there's a discrepancy. It demonstrates that the breach was authorized and documented. I’ve seen this simple entry save a company from being penalized for a "broken seal" violation. It provides the full story, from start to finish. A complete story is a defensible story.
Conclusion
A security seal logbook is more than a record; it's your evidence. Tracking these seven data points transforms a simple list into a powerful Chain of Custody that protects your assets, your reputation, and your bottom line.
Build Your Evidentiary Chain with ProtegoSeal
Stop leaving yourself exposed. ProtegoSeal provides not only the high-quality, uniquely numbered seals you need but also the expertise to help you build a logbook system that creates a legally-sound Chain of Custody. Contact us to create a security program that stands up to scrutiny.