Are you relying on a single security feature to protect your assets? This single point of failure is what professional thieves are trained to exploit, leaving your cargo vulnerable to undetectable breaches.
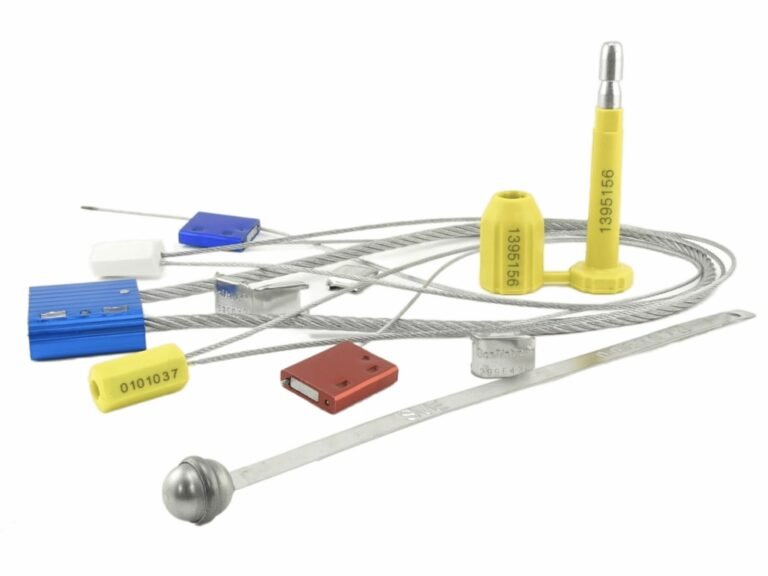
The four core tamper-evident technologies—engineered breakpoints, layered adhesives, optical tech, and unique serialization—work together to create a multi-layered defense. Each provides a different type of forensic evidence, making tampering impossible to hide.

The four technologies I'm about to show you are not competing options. They are the "four cornerstones" for building a defense-in-depth security system. Each represents a different forensic strategy: physical evidence, surface evidence, identity evidence, and digital evidence. In my experience, the most powerful security solutions never rely on a single, "strongest" technology. Instead, they intelligently combine these cornerstones, creating a mutually reinforcing evidence network that leaves a tamperer with nowhere to hide.
Type 1: Engineered Breakpoints — Leaving Permanent Physical Evidence of Tampering?
Think a security seal that's been super-glued back together can still be trusted? This is a classic tampering technique that a simple lock design completely fails to prevent, leaving you blind to a breach.
An engineered breakpoint is a part of a seal intentionally designed to fracture in a specific, permanent way when force is applied. This makes it impossible to repair or reassemble the seal without leaving obvious, irreversible physical damage.

This is the most fundamental forensic strategy: leaving behind undeniable physical evidence. Think of it as a security device that is designed to self-destruct upon attack.
In our plastic pull-tight seals, for example, the locking jaw that grips the seal's tail is designed to shear off if someone tries to reverse it. It's a one-way street. Once broken, it's broken forever. There is no ambiguity. This technology provides a simple, binary answer to the question, "Has this been compromised?" If the breakpoint is intact, it has not. If it is broken, it has. It is the physical "smoking gun" that proves an unauthorized attempt at entry.
Type 2: Layered Adhesives — Revealing a "VOID" Warning Upon Removal?
How can you be sure someone hasn't peeled off a security label, opened your package, and then carefully stuck the same label back on? A standard adhesive label makes this type of tampering easy and invisible.
Layered adhesive technology uses a multi-layer construction in tapes and labels. When someone tries to remove it, the layers separate, revealing a hidden warning message, typically "VOID" or "OPENED," that cannot be erased or hidden.

This is our second forensic strategy: collecting surface evidence. It turns the surface of your carton or product into an active security component. The magic is in the adhesive chemistry. I've worked with this technology for years, and its effectiveness is in its simplicity. A standard label relies on a single layer of glue. Our tamper-evident labels use a system where the top film layer has a weak bond to a pattern-printed adhesive layer underneath. When peeled, the top layer lifts off, but the patterned adhesive—the "VOID" message—is specifically designed to have a much stronger bond to the cardboard or plastic surface it's on. It permanently delaminates, leaving the warning message behind. This makes it impossible to reapply the label without showing clear, unambiguous evidence of the initial removal.
Type 3: Holographic & Optical Tech — Creating a Visual Fingerprint That Can't Be Copied?
In an age of high-resolution scanners and printers, how can you be sure a security label isn't just a clever counterfeit? A simple printed logo or design can be easily replicated by a determined counterfeiter.
Holographic and other optical technologies create complex, multi-dimensional images that are nearly impossible to replicate without the original master equipment. This OVD (Optical Variable Device acts as a unique visual fingerprint, providing instant and high-security authentication.

This is our third strategy: establishing identity evidence. A hologram's security comes from its microscopic complexity. It's not an image printed with ink; it's a micro-embossed structure that diffracts light in a very specific way. To fake it, a counterfeiter would need access to the same incredibly expensive and specialized laser-etching technology used to create the original master hologram. Cheaper replication methods, like scanning, can't capture the hologram's depth and light-shifting properties. This is why holograms are used on currency and credit cards. When applied to a security seal or label, it serves as an instant, non-replicable mark of authenticity. It proves that the seal itself is genuine and not a fraudulent copy.
Type 4: Unique Serialization — Giving Every Item a Traceable Digital Identity?
If a thief cuts off one seal and replaces it with an identical-looking, brand-new one, how could you ever prove a switch occurred? Without individual identification, all your seals are interchangeable and untraceable.
Unique serialization gives every single security seal its own distinct name—a serial number, barcode, or QR code. This transforms a physical object into a traceable data point in your chain of custody.

This final cornerstone is our fourth forensic strategy: creating digital evidence. This is arguably the most powerful technology in the entire system. A unique serial number, especially when paired with a barcode for easy scanning, creates a digital breadcrumb trail. The process is simple: scan the seal at origin when it's applied, and scan it again at the destination before it's removed. The numbers must match. This system makes the "replace with an identical copy" tactic completely useless. The thief can't guess the original number, and they can't create a new seal with that number. In my view, this technology is what elevates a simple lock into a true component of a modern supply chain security system. It allows you to trust, but more importantly, to verify.
How to Choose the Right Combination of Technologies for Your Product?
Do you feel you have to pick just one of these technologies to be your "silver bullet"? The reality is, a single defense is rarely enough. The most sophisticated threats require a more sophisticated, layered response.
The smartest security solutions combine these technologies. A high-value product should be protected by a seal that leverages multiple forensic strategies at once: physical, surface, identity, and digital evidence.

Think like a security architect. Your goal is to create a system where each technology covers the potential weaknesses of the others. Here's a real-world example of how we combine these cornerstones for ultimate protection:
- A high-security plastic seal for a duty-free cart. It uses an engineered breakpoint (physical evidence) so it can't be re-glued, and a unique serial number (digital evidence) so it can't be secretly replaced.
- A security label for pharmaceuticals. It uses layered adhesive (surface evidence) to show if the box was opened, a hologram (identity evidence) to prove the label is authentic, and a QR code (digital evidence) for tracking.
By layering these tactics, you create an evidence network that is incredibly difficult for any adversary to defeat without leaving a trace. You force them to overcome not just one barrier, but four different types of forensic traps.
Conclusion
Stop relying on a single security feature. A truly robust solution is a defense-in-depth system built on four cornerstones: engineered breakpoints, revealing adhesives, holograms, and unique serialization.
Build Your Evidence Network with ProtegoSeal
At ProtegoSeal, we are masters of combining these technologies to create custom security solutions. We can help you architect the right mix of forensic strategies for your specific needs. Contact me to design your multi-layered defense.