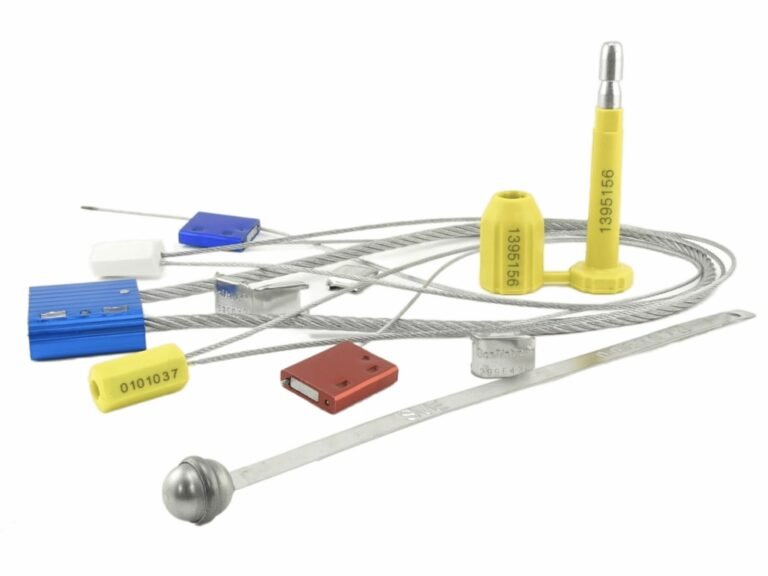
Are you relying on a single security feature to protect your most valuable assets?
In the world of supply chain security, a "single point of failure" is exactly what professional thieves are trained to exploit. If your defense relies on just one lock or one sticker, you are leaving your cargo vulnerable to undetectable breaches.
To truly secure a shipment, you need a system that forces an attacker to overcome multiple, distinct hurdles. This is known as Defense-in-Depth.
The four core tamper-evident technologies—Engineered Breakpoints, Layered Adhesives, Optical Tech, and Unique Serialization—are not competing options. They are the four cornerstones of a robust security strategy. Each provides a different type of forensic evidence (Physical, Surface, Identity, and Digital), creating a mutually reinforcing network that leaves a tamperer with nowhere to hide.

Below, we analyze how these four technologies work together to create an unbreakable chain of custody.
1. Engineered Breakpoints: Permanent Physical Evidence
The most fundamental question in security is: "Has this container been opened?" Engineered breakpoints provide a binary, undeniable answer.
A common flaw in cheap locks is that they can be cut and glued back together. An engineered breakpoint is a structural weak point intentionally integrated into the seal's design (such as the locking mechanism of a plastic seal). It is calculated to fracture in a specific, catastrophic manner when stress is applied, complying with standards like ISO 17712 for mechanical seals.
How It Works
In our plastic pull-tight seals, the locking jaw is designed to be the "sacrificial lamb." If someone attempts to reverse the seal or force it open, the jaw shears off completely.
- The Security Advantage: It creates a one-way failure. Once the material stress limit is reached, the component separates permanently. It cannot be melted, glued, or reassembled without leaving jagged, obvious scarring.
- Forensic Type: Physical Evidence. It serves as the "smoking gun" that proves an unauthorized entry attempt occurred.

2. Layered Adhesives: The "VOID" Surface Warning
How do you stop a thief from peeling off a label, stealing the contents, and sticking the label back on? A standard adhesive label makes this invisible theft easy.
Layered adhesive technology transforms the surface of your packaging into an active alarm system. It utilizes a chemically complex, multi-layer construction that is designed to delaminate (split apart) under peeling force.
The Mechanism of Action
This technology relies on differential bond strengths.
- Top Layer: The visible film/label.
- Release Pattern: A "VOID" or "OPENED" message printed in a specific release agent.
- Bottom Adhesive: A high-tack glue that bonds aggressively to your carton.
When someone attempts to lift the label, the bond between the Top Layer and the Release Pattern breaks before the bond between the Adhesive and the box. The label "self-destructs," leaving the "VOID" message permanently transferred onto the box surface. This is critical for maintaining integrity in high-value packaging.
- The Security Advantage: It effectively ruins the label for reuse. You cannot "un-peel" the VOID message.
- Forensic Type: Surface Evidence. It makes the carton itself a witness to the crime.

3. Holographic & Optical Tech: The Uncopyable Identity
In an age of high-resolution digital scanning, a simple printed logo is not security—it's decoration. Counterfeiters can replicate standard ink printing in minutes.
Holographic and OVD (Optical Variable Device) technologies serve as the visual "fingerprint" of your security seal. They create complex, multi-dimensional images that shift and change based on the viewing angle.
Why It Beats Counterfeiters
A true security hologram isn't printed with ink; it is micro-embossed. It consists of microscopic grooves that physically diffract light waves.
- Barrier to Entry: Replicating a master hologram requires expensive, specialized laser-etching equipment.
- Visual Authentication: Personnel can instantly verify authenticity with the naked eye. If the logo doesn't float, shift colors, or show depth, it's a fake.
- Forensic Type: Identity Evidence. It proves that the seal originated from your facility, not a counterfeiter's printer. Learn more about our custom security solutions to see how we integrate holograms.

4. Unique Serialization: Traceable Digital Evidence
If a thief cuts off your seal and replaces it with a brand-new, identical one, how would you know? Without data, you wouldn't. This is the "replacement attack," and it defeats most physical security.
Unique Serialization assigns a distinct digital identity—a sequential number, barcode, or QR code—to every single seal produced.
The Digital Chain of Custody
This transforms a piece of plastic into a trackable data point.
- Origin: The seal ID is scanned and linked to the shipping manifest.
- Transit: The seal is verified at checkpoints.
- Destination: The receiver scans the seal. If the numbers don't match, the cargo is rejected.
- The Security Advantage: It makes the "replacement attack" impossible. A thief cannot guess the random serial number of the original seal, nor can they manufacture a duplicate on the spot. Using standards like GS1 Barcodes allows for global interoperability.
- Forensic Type: Digital Evidence. It allows you to audit the integrity of the shipment remotely.

Strategy: Combining the 4 Cornerstones
The most sophisticated security breaches require a layered response. A high-value product should never rely on just one of these technologies.
The "Protego" Approach:
We recommend a "Hybrid Seal" strategy. For example, a pharmaceutical shipment might use a label that combines:
- Hologram (Identity) to prove it's not a fake.
- Layered Adhesive (Surface) to show if it was peeled.
- QR Code (Digital) for track-and-trace.
- Perforations (Breakpoints) so it tears if pulled.

Frequently Asked Questions (FAQ)
Q: What is the difference between "Tamper-Proof" and "Tamper-Evident"?
A: "Tamper-proof" implies entry is impossible (which is rarely true). "Tamper-evident" means that entry is possible, but it will result in irreversible, visible damage that alerts the receiver. Our technologies focus on evidence to deter theft and identify breaches immediately.
Q: Can VOID tape be reapplied after removal?
A: No. Once the adhesive layers separate and the "VOID" message is revealed, the chemical bond is broken. Reapplying the tape will not hide the "VOID" text, and the tape will lose its tackiness.
Q: How does unique serialization prevent cargo theft?
A: It prevents the "cut and replace" tactic. Thieves often carry generic seals to replace the ones they break. By scanning a unique barcode at the destination, you ensure the seal on the truck is the exact same one that left the warehouse.
Build Your Evidence Network with ProtegoSeal
Don't leave your assets exposed to simple attacks. At ProtegoSeal, we specialize in combining these four technologies into custom security solutions tailored to your supply chain.
Contact us today to design a multi-layered defense system that leaves tamperers with nowhere to hide.