You’ve invested in a heavy-duty lock, believing your assets are safe. But you arrive to find the lock cut and your container empty. The lock alone was just a single point of failure.
To truly secure a shipping container, you must create a multi-layered security system. This means combining robust physical hardware, like high-security locks and tamper-evident seals, with strict procedural controls, such as secure parking and a rigorous inspection protocol. This integrated approach makes theft too difficult and risky.

I had a client who learned this the hard way. He spent hundreds of dollars on a top-of-the-line lock for his container, which was staged in a public lot. Thieves ignored the lock, cut through the container wall with a portable saw, and emptied it. His single point of defense failed because he didn't have a system. Securing a container is an engineering project, not a shopping trip. It’s about building a system where each part supports the others.
What’s the First Line of Defense? Selecting a Robust Container Lock?
You see a cheap lock and think you're saving money. A thief sees that same lock and thinks it's an open invitation. Your first physical barrier must be a meaningful one.
The first line of defense is a high-quality, heavy-duty lock designed to resist common brute-force attacks. Look for locks made from hardened steel with shrouded shackles that offer no room for bolt cutters. This initial step immediately increases the time and tools required for a break-in.

A strong lock is about buying time and creating noise. As I tell my clients, a thief's two biggest enemies are time and attention. A cheap lock can be snapped in under 10 seconds. A high-quality lock may require several minutes of grinding with a power tool, creating a massive amount of noise and drawing unwanted attention. This significantly raises the risk for the criminal. The lock’s job isn’t to be unbreakable; it’s to make breaking it an unattractive, high-risk proposition. This is the first, crucial layer of your security system.
Key Features of a High-Quality Container Lock
When selecting a lock, don't just look at the brand. Look at the engineering.
| Feature | Why It Matters | Lock Types |
|---|---|---|
| Hardened Steel Body | Resists drilling, cutting, and grinding attacks. | Heavy-Duty Padlocks, Puck Locks |
| Shrouded Shackle | Hides the shackle from bolt cutters, leaving no weak point to attack. | Puck Locks, Shrouded Padlocks |
| Pick-Resistant Core | Contains complex pin systems that are difficult for thieves to manipulate. | High-Security Padlocks |
| Weather Resistant | Prevents rust and seizure, ensuring the lock works when you need it. | Most quality outdoor-rated locks |
Why a Lock-Only Defense is Incomplete?
Your container is secured with the best lock money can buy. But a determined thief simply cuts the door hinge pins, bypasses your expensive lock entirely, and accesses the cargo.
A lock-only defense is incomplete because it’s a single point of failure in a system with multiple vulnerabilities. A lock only protects the hasp. Thieves can attack the container walls, the roof, or the door hinges. More importantly, a lock provides zero evidence of when or how it was compromised.
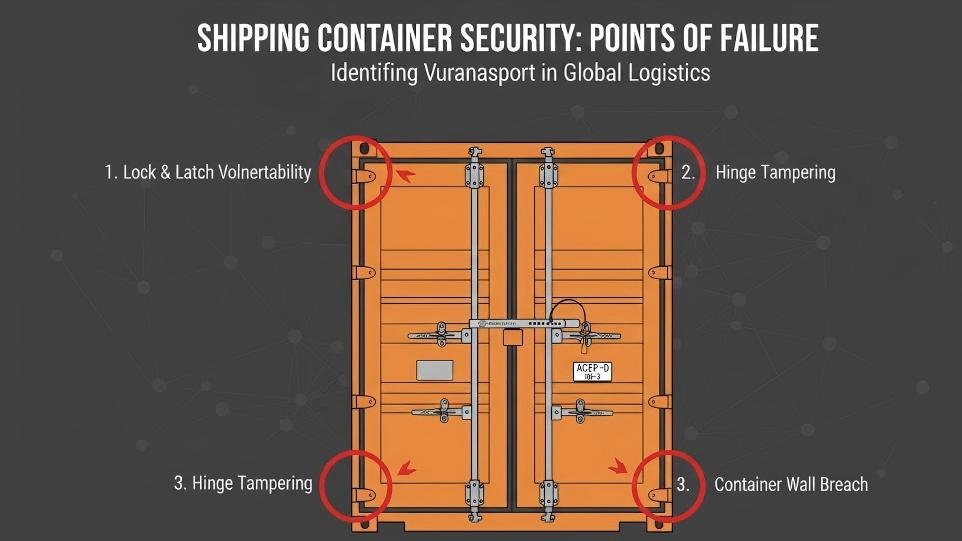
This is the an important point I always stress with my clients: your lock is a deterrent, not an alarm. It can be cut, picked, or completely bypassed. If it's removed, it tells you a breach occurred, but it can’t prove when the breach happened or if it was an "inside job." It creates a simple yes/no security state (locked/unlocked) with no audit trail. To build a truly secure system, you need another layer that does what the lock can't: provide undeniable, time-stamped evidence. This moves your security from simple prevention to active detection and accountability.
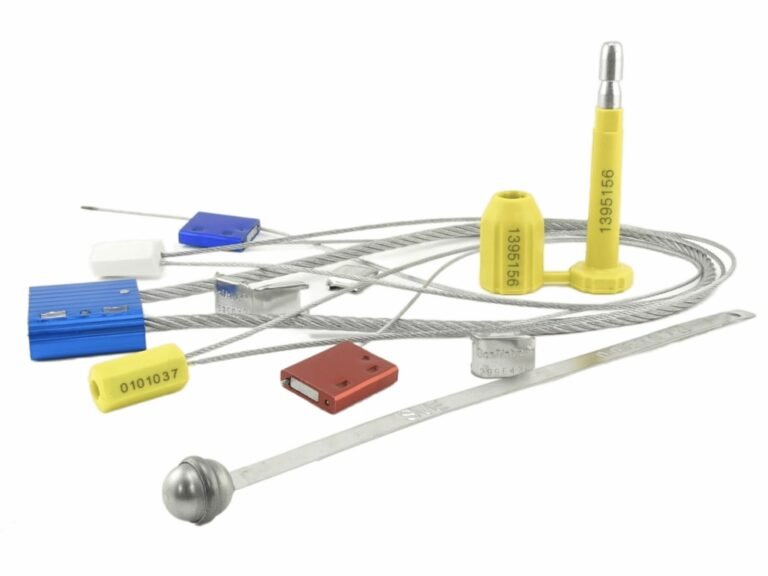
How Do High-Security Seals Create a Tamper-Evident Layer?
A container arrives with its lock missing, and the cargo is gone. The driver blames the warehouse, the warehouse blames the driver, and you're stuck in the middle with a huge financial loss.
A high-security bolt seal adds the critical layer of accountability. Unlike a reusable lock, an ISO 17712 compliant bolt seal has a unique serial number and is designed for single use. Once broken, it can't be reassembled. This creates undeniable proof that the container was opened.

This is where hardware meets process. The lock's job is to delay entry. The seal's job is to record that entry. They are two different tools for two different jobs, and they work together perfectly. When you apply a seal, you must record its number on the shipping documents. This starts a chain of custody. If the seal is broken or the number doesn't match upon arrival, the argument stops. The burden of proof immediately shifts to the party who last handled the container. This simple, inexpensive device can save you from thousands of dollars in liability disputes.
| Security Layer | Primary Function | Question It Answers |
|---|---|---|
| High-Security Lock | Deter & Delay: Makes physical entry difficult and time-consuming. | "Is the container physically hard to get into?" |
| High-Security Seal | Detect & Document: Provides undeniable proof of entry with a unique ID. | "Has the container been opened since it was sealed?" |
Is Your Container's Parking Location Secure?
You've got the best lock and seal, but your container is parked in a dark, unmonitored corner of a public lot. You’ve given thieves the two things they need most: privacy and time.
The physical location where your container is stored is a critical, and often overlooked, security layer. A secure location acts as a force multiplier for your locks and seals. Parking in a well-lit, fenced yard with CCTV surveillance and controlled access dramatically increases the risk of a thief being seen and caught.

This is a core principle of Crime Prevention Through Environmental Design (CPTED). You are designing an environment that is hostile to criminal activity. A thief might be willing to spend ten minutes grinding off a lock in a secluded area, but they won't do it under a bright floodlight and in front of a surveillance camera. I always advise clients that the monthly cost of secure parking is not an expense; it's insurance. It protects the hardware you've invested in and reinforces your entire security system. An isolated container is a target. A monitored container is a risk. Thieves always avoid unnecessary risk.
Establish an Unbreakable Inspection and Documentation Protocol?
All your hardware is useless if no one is checking it. A broken seal that goes unnoticed for days is no better than having no seal at all.
The final, binding layer of your security system is a strict, mandatory protocol for inspection and documentation. This means that at every single handover point—from your facility to the driver, from the driver to the port—a trained individual must physically check both the lock and the seal, and document their integrity and serial number.

This is the "closed-loop" part of the system. It’s what connects all the other layers. Your protocol is the set of rules that ensures your hardware is being used correctly. It turns passive objects (locks and seals) into active security checkpoints. A solid protocol should include:
- Seal Application Log: Who applied the seal, when, and what was the number?
- Photo Documentation: Taking a clear photo of the sealed and locked container before it departs.
- Handover Inspection: The receiving party must confirm the lock is intact and the seal number matches the manifest before signing for the container. Any discrepancy must be noted and reported immediately.
This formal process creates accountability at every step. It ensures that if a breach occurs, you can pinpoint exactly when and where it happened, transforming a massive security hole into a manageable and identifiable problem.
Conclusion
A single lock is just an invitation for a prepared thief. A true theft-proof system binds robust locks and seals with secure locations and unbreakable inspection protocols, making your container an unprofitable target.
Build Your Closed-Loop Security System with ProtegoSeal
Stop relying on a single point of failure. The ISO 17712 compliant high-security bolt seals from ProtegoSeal are the cornerstone of a modern, accountable security protocol. Contact us to integrate the critical evidence layer into your system.