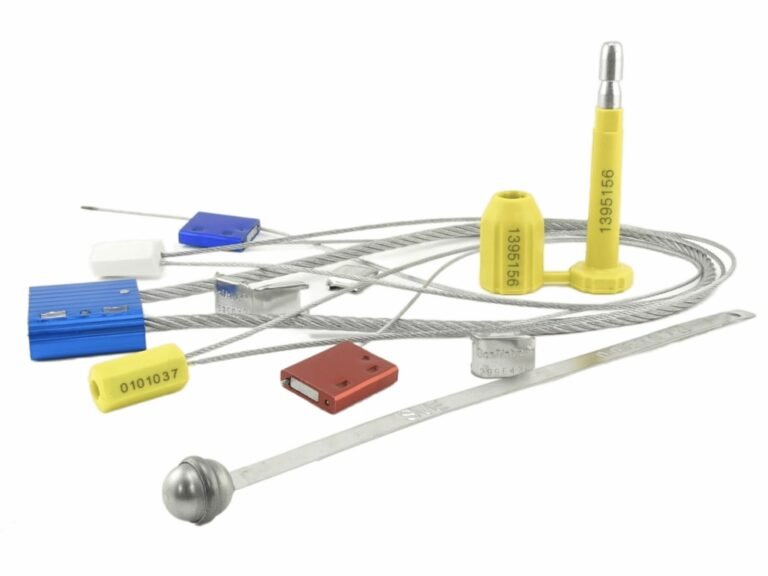
You hear the term "tamper-evident" used for everything from foil on a medicine bottle to a simple padlock. You assume they all offer the same level of security information.
This misunderstanding is a critical security vulnerability. Relying on a device that isn't truly tamper-evident means you may never know your assets were compromised until it's too late, leaving you with no proof and significant losses.
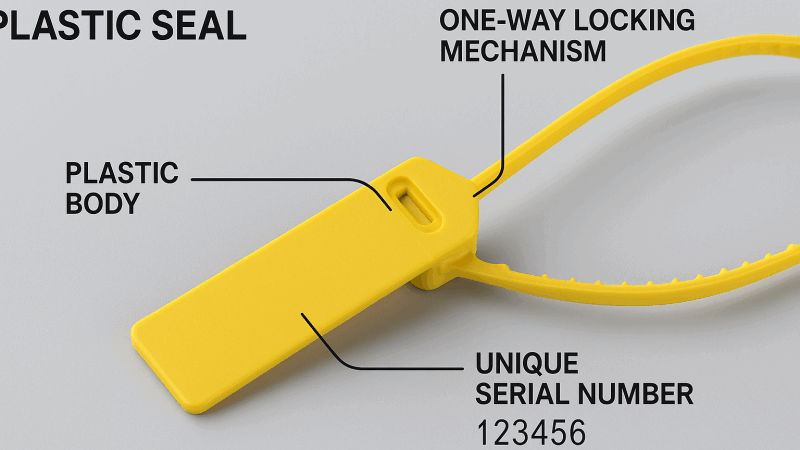
A "tamper-evident" seal is a single-use device whose primary purpose is to provide clear, irreversible proof if it has been opened or compromised. Plastic seals are the best example because they perfectly integrate a one-time locking mechanism, materials that visually scar, and a unique serial number.
When I started in this industry, I thought the goal was to make a seal as hard to open as possible. It took me years, especially from my time in quality control inspecting thousands of seals, to understand the real purpose. “Tamper evidence” isn't about brute strength; it’s about creating a perfect witness. It’s a system designed to provide clear, instant, and irreversible proof of an attack.
A plastic seal is the textbook example of this concept. It’s not because it's the strongest in any single category, but because it perfectly balances "richness of evidence" with "ease of understanding." It masterfully combines mechanical structure, material properties, and information identifiers into one small, powerful package. It’s the introductory textbook to tamper-evidence, while a high-security bolt seal is more like an advanced monograph for specific, high-risk scenarios.
Unpacking the Core Concept: Tamper-Evidence is All About Irreversible Proof?
You use a zip tie to "seal" a bag. It's cut and replaced with an identical one. Would you ever know?
This is the key question that separates simple fasteners from true security devices. The core principle of tamper-evidence is creating a state that, once changed, can never be perfectly restored.
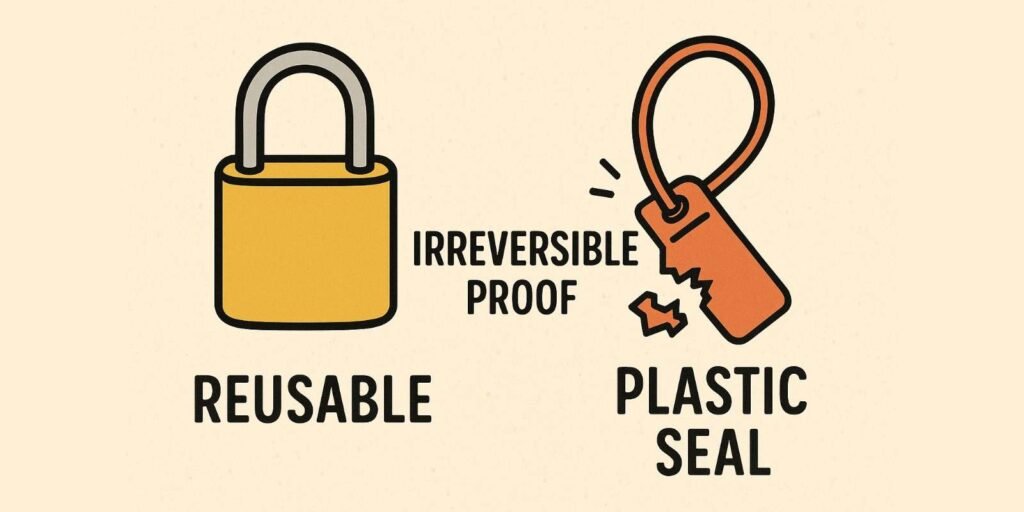
The entire philosophy of a tamper-evident device is not just to secure an item, but to preserve a record of its integrity. It serves as a guarantee that "from the moment I sealed this until the moment you inspected it, its state has not changed." Unlike a simple padlock that can be picked and re-locked, a true tamper-evident seal is designed for a one-way journey. Its destruction is a feature, not a failure. This idea is central to maintaining a secure chain of custody, where each transfer of an asset can be verified. The moment that chain is broken, the seal provides the definitive, undeniable evidence. It’s a promise of integrity, and if that promise is broken, the seal is designed to tell you loudly and clearly.
Embodying Physical Proof: How a Plastic Seal's One-Time Locking Mechanism Fulfills the Tamper-Evident Principle?
You apply a seal and pull it tight. Why can't a thief just pull it back out?
This is where the genius of the mechanical design comes into play. The plastic seal's locking mechanism is a marvel of simple, effective engineering designed for a single purpose: to never go backward.
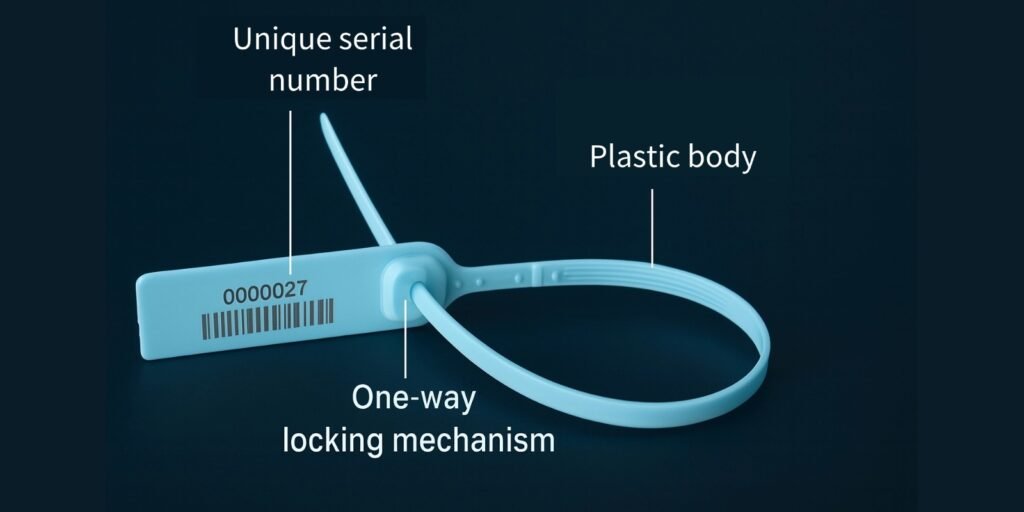
Inside the head of most plastic pull-tight seals is a small metal or plastic locking jaw. It's angled like a one-way gate. When you pull the tail of the seal through, the teeth on the tail slide easily past the jaw. But if you try to pull it back out, the jaw bites into the plastic, locking it permanently in place. There is no key. There is no combination. The only way to remove it is to destroy it—by cutting the strap. This simple, one-time-use mechanical design is the first and most fundamental layer of the tamper-evident system. It provides the physical proof. It ensures that any access requires a destructive act, an act that cannot be undone, turning the seal itself into the first piece of evidence.
Guaranteeing Visual Proof: Why Plastic's Material Properties Are Ideal for Creating Evidence of Tampering?
A thief tries to melt the seal back together with a lighter or pry it open. How does the plastic itself betray them?
This is the second dimension of proof: the material's inherent inability to hide its scars. The choice of plastic (like HDPE or PP) is deliberate because these materials are excellent at showing evidence of attack.
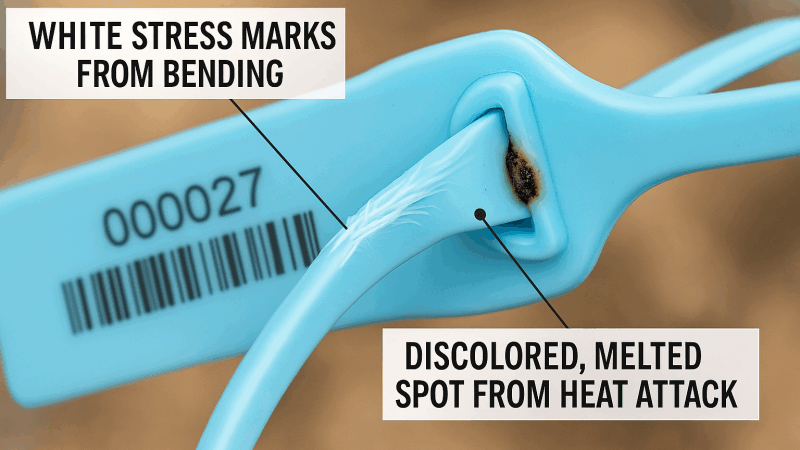
I've spent countless hours in a lab trying to defeat seals without leaving a mark. It taught me that these plastics are fantastic "witnesses." They provide visual proof in several ways:
- Stress Whitening: When you bend or stretch a plastic like HDPE, it creates permanent white marks (known as stress whitening). This is a clear indicator of physical manipulation.
- Heat Deformation: If a thief tries to use a heat gun or lighter to manipulate the lock, the plastic will noticeably melt, discolor, and deform. It's impossible to restore it to its original smooth finish.
- Chemical Attack: Attempting to use solvents to weaken the lock will cause the plastic to swell, soften, or change color.
The plastic isn't just a housing for the lock; it's an active part of the evidence system. It's chosen because it's a poor liar. It readily and permanently displays any signs of tampering.
Forging the Data Proof Chain: How Unique Serial Numbers Elevate Tamper-Evidence from Physical to Managerial?
The seal is broken. Was it the original seal, or was it replaced with an identical one?
This is where the third dimension of proof comes in, elevating the seal from a simple physical device to a component in a management system. The unique serial number provides the data proof.

A plastic seal without a serial number is only half a solution. The unique, laser-engraved serial number ensures that the seal cannot simply be cut off and replaced with a new, identical-looking one. This is the cornerstone of building a robust audit trail. The process is simple but powerful:
- Record: When the seal is applied, its unique number is recorded on the shipping manifest or in a digital log.
- Verify: When the asset arrives, the recipient first checks that the seal is physically intact.
- Confirm: Their second, crucial check is to confirm that the serial number on the seal matches the number in their documents.
Any discrepancy—a broken seal or a mismatched number—is an immediate, non-negotiable red flag that triggers an investigation. This transforms the seal into a data point, integrating it into a larger security management system.
The Final Verdict: Why Padlocks or Tapes Can't Illustrate Tamper-Evidence as Perfectly as a Plastic Seal?
So, why isn't a roll of "security tape" or a simple padlock the best example?
Because they fail to perfectly integrate all three dimensions of proof in a single, easy-to-understand device. They each have a fatal flaw in their evidence mechanism.

Let's break it down:
- Padlocks: A standard padlock is tamper-resistant, not tamper-evident. An expert can pick it and re-lock it, leaving no evidence of entry. It lacks a true one-time locking mechanism and has no inherent data proof (unless you use a uniquely numbered one, which is rare and still pickable).
- Security Tape: While tape shows a "VOID" message when peeled (visual proof), it's easy for a thief to cut open the box seam next to the tape, remove the contents, and re-glue the box. The tape itself remains perfectly intact. It lacks mechanical proof of container integrity.
- The Plastic Seal: It alone provides the perfect trifecta:
- Mechanical Proof: Cannot be opened without being destroyed.
- Visual Proof: The material shows evidence of any attack.
- Data Proof: The unique serial number prevents replacement.
This is why the humble plastic seal is the undisputed, textbook champion of the tamper-evident concept.
Conclusion
A tamper-evident device is a system that provides irreversible physical, visual, and data proof of interference. The plastic seal is its perfect embodiment, elegantly combining all three principles into a single, effective, and easy-to-understand product.
See the Textbook Example of Tamper-Evidence with ProtegoSeal
Don't just secure your assets; make them talk. At ProtegoSeal, our plastic seals are designed to be the perfect "witnesses," embodying all core principles of tamper evidence. Contact us to see how the textbook example can strengthen your real-world security.