You're considering RFID seals to slash errors and improve visibility, but the project seems overwhelming. You're afraid of a failed implementation, wasted investment, and causing massive disruption to your operations.
A successful RFID seal project is not about buying seals, it's about building a complete automated data system. The key is to perfectly integrate three parts: the RFID seal (data source), the reader (collection hardware), and the software (processing platform) with your existing business systems.
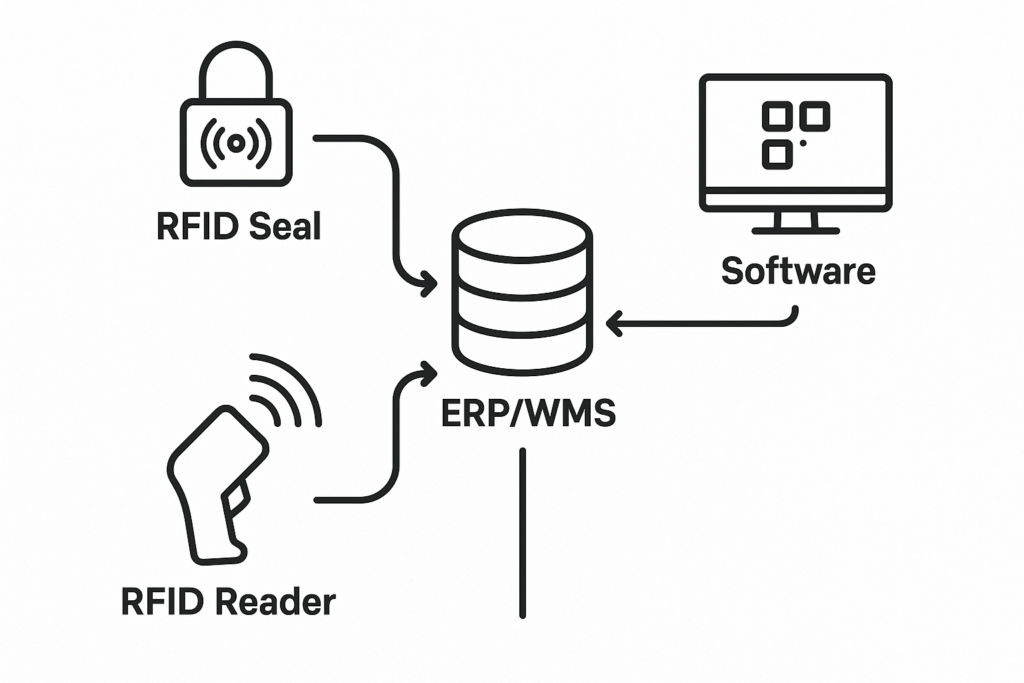
I always start my RFID consultations with the same core idea: this project is essentially building a small, automated data company within your logistics operation. The RFID seal itself is your field reporter—the data source. The readers are your data collection hardware. And your software is the central intelligence desk—the processing platform where decisions are made. The success of the entire project depends on how well these three components talk to each other and, most importantly, how they are integrated into your existing ERP or Warehouse Management System (WMS) to hit your specific business goals. This guide will walk you through how to build that system, step by step.
How Do You Commission Seals to Create Your Data Source?
You have a box of new RFID seals, but right now they are just anonymous pieces of plastic. Without a proper identity, they are completely useless and will only create confusion in your system.
Commissioning is the process of assigning a unique digital identity to each physical seal and linking it to a specific asset in your database. This action transforms a generic seal into a specific, trackable data source.

This first step is what gives your "field reporter" its assignment. Before a seal is ever attached to a container or pallet, it needs to know what it represents. This process of data association is foundational. Typically, it works like this:
- Scan the Seal: A handheld RFID reader is used to read the seal's unique, unchangeable Tag ID (TID).
- Scan the Asset: The worker then scans the barcode of the pallet, container, or master carton that the seal will be attached to.
- Create the Link: The software "marries" these two pieces of information. Now, your WMS knows that RFID Seal
TID#...E4F8is equivalent to "Pallet of Medical Supplies, PO #78910."
From this moment on, whenever a reader detects that seal's unique radio signal, your system doesn't just see a random number; it sees the specific asset you assigned to it. Skipping or poorly managing this step is the #1 reason early-stage RFID projects fail.
Where Should You Strategically Place Readers for Data Collection?
You've installed expensive RFID readers, but you're getting missed reads and inaccurate data. Your "automated" system now requires frustrating manual rescans, completely defeating the purpose of the investment.
Strategic reader placement is crucial. You must install your "collection hardware" at key logistical chokepoints—like dock doors, conveyor belts, and warehouse entryways—to create reliable, automated data capture zones.
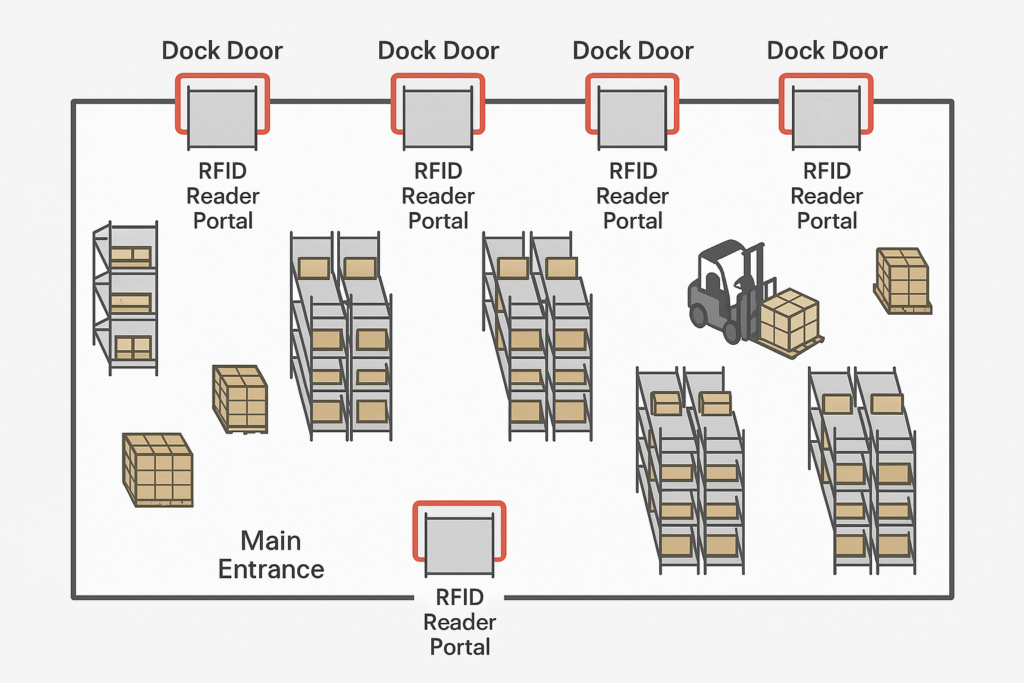
You have to position your hardware where the story is happening. The goal is to gather data without interrupting the operational flow. This requires a basic understanding of your facility's radio-frequency (RF) environment, as signals can be affected by metal and liquids.
Here are the most effective placements:
| Location | Purpose | Strategic Value |
|---|---|---|
| Dock Door Portals | Shipping & Receiving | Automatically logs every sealed asset as it enters or leaves a truck, verifying manifests in real-time. |
| Conveyor Tunnels | In-line Processing | Scans individual sealed cartons as they move along a conveyor, allowing for automated sorting and routing. |
| Warehouse Gates | Internal Movement | Tracks the movement of sealed assets between different zones (e.g., from bulk storage to picking area). |
| Forklift-Mounted Readers | Dynamic Locating | Allows operators to find a specific sealed asset within a massive warehouse or yard. |
I advised a client who initially placed readers on the ceiling. They got terrible read rates because the forklifts' metal masts were blocking the signals. We moved the readers to side-facing portals at the dock doors. Their read rate immediately jumped to 99.8%, and the system finally delivered on its promise.
How Does RFID Automate Your Shipping and Receiving Chokepoints?
Your shipping and receiving docks are a chaotic mix of manual scanning, paper checklists, and inevitable human error. This leads to costly mis-shipments and long driver wait times.
By integrating reader hardware with your software platform, you transform chokepoints into intelligent, automated gates. The system validates entire shipments hands-free, confirming the right goods get on the right truck, every time.

This is where the magic happens—where the data source, hardware, and platform work together to solve a major business problem.
The Transformation of a Dock Door
| Before RFID (Manual Process) | After RFID (Automated Process) |
|---|---|
| Driver gives manifest to clerk. | Manifest is pre-loaded in the WMS. |
| Forklift operator loads pallet onto truck. | Forklift operator loads pallet onto truck. |
| Clerk walks to truck, finds pallet, scans barcode. | As pallet passes through the portal, it's scanned automatically. |
| Clerk checks scanner against paper manifest. | WMS instantly validates the seal ID against the manifest. |
| Result: 2-5 minutes per pallet. Prone to error. | Result: 2-5 seconds per pallet. Highly accurate. |
When the last correct pallet is loaded, the system can automatically generate a confirmation, update the inventory, and approve the truck for departure. You've just eliminated the single biggest source of shipping errors and dramatically increased your throughput.
How Do You Leverage Seal Data Beyond Security?
You're viewing RFID seals as just a high-tech lock. This mindset causes you to miss the biggest ROI opportunities: operational intelligence and inventory accuracy.
The continuous stream of data from your seals is a goldmine. You can leverage it to conduct real-time inventory counts, automate dispatch verification, and eliminate the need for manual cycle counting.

A security seal provides a single data point: "tampered" or "not tampered." An RFID seal provides a continuous story: "I am here. Now I'm here. Now I'm leaving." Here’s how to use that story:
- Real-Time Inventory: Imagine knowing your exact inventory count, 24/7, without ever sending a team out to manually count boxes. By placing readers strategically, your system always knows what is in a specific zone, creating a "self-auditing" warehouse.
- Automated Dispatch Verification: The system can verify not just the contents, but the truck itself. By placing a simple RFID tag on your trailers, the system can confirm "Pallet #789" is being loaded onto "Trailer #204," preventing disastrous mix-ups.
- Last-Seen Location: If a sealed asset goes missing, you don't have to guess where it was lost. Your system can provide a definitive "last-seen" location and time (e.g., "last read at Dock Door 7, Tuesday, 4:32 PM"), shrinking search times from days to minutes.
How Do You Handle Real-Time Alerts When a Seal is Breached?
An RFID tamper-evident seal is broken mid-transit. If you only find out when the truck arrives, it's too late. The evidence is cold, and the thief is long gone.
Your software platform can be configured to trigger instant, real-time alerts. When a seal's status changes to "tampered" or if it's detected in an unauthorized zone, the system sends immediate notifications to security and management.

This is the proactive security promise of an RFID system. It's not just a rec2025-10-15 17:37:34 Wednesdayord-keeping tool; it's a real-time alarm system. This process is known as exception handling.
Here’s how it works:
- A Trigger Event Occurs: An RFID seal with tamper-detection capabilities is broken, or a sealed asset passes through a reader in an unauthorized "red zone."
- The Platform Executes Logic: The software sees this event and recognizes it as an exception based on the rules you've set (e.g., "This seal should not be breached before reaching its destination").
- An Alert is Sent: The system automatically sends an email, SMS, or dashboard alert to the relevant personnel.
- Action is Taken: The alert can include the seal ID, the asset it was attached to, and the precise location and time of the event. Your security team can now respond immediately, not hours or days later. This transforms your security posture from reactive to proactive.
Conclusion
A successful RFID implementation is a strategic integration of seals, readers, and software. By viewing it as a complete data system, you can move beyond simple security to revolutionize your inventory accuracy, shipping speed, and operational intelligence.
Build Your Automated Data System with ProtegoSeal
Whether you're just beginning to plan or are ready to implement, building the right system starts with the right components. At ProtegoSeal, we provide the advanced RFID seals and expert guidance you need to successfully integrate your data source, hardware, and software. Contact us to design your system for success.