Are you fighting a losing battle against electricity theft with stronger locks and thicker meter boxes? This physical-only approach misses the real battlefield: the battle of information, deterrence, and legal evidence.
Modern security seals are not walls; they are a low-cost, trusted intelligence network. They deter theft not with strength, but by creating an undeniable, legally actionable audit trail of any tampering attempt, turning a physical act into a documented crime.

The biggest mistake I see utility companies make is thinking of security seals as a form of physical defense. This is old thinking. A modern security seal's core value is not in physical obstruction, but as a crucial, tamper-proof "data collection terminal" in your grid's audit chain. We are not talking about defense; we are talking about deterrence and evidence gathering. The seal is not a wall; it is an intelligence network deployed at your grid's most vulnerable endpoints. Its power lies not in its plastic shell, but in the message it sends to a potential thief: "Your actions are being recorded, and you will leave behind irrefutable legal evidence." This is a psychological war based on information, not just a physical one.
Unlocking the Mechanism: How Tamper-Evident Seals Physically Stop Fraud?
Do you believe a plastic seal can physically stop a determined criminal? This is a misunderstanding of the seal's true mechanism. It’s not about stopping the first attempt, but ensuring there is no second chance to hide it.
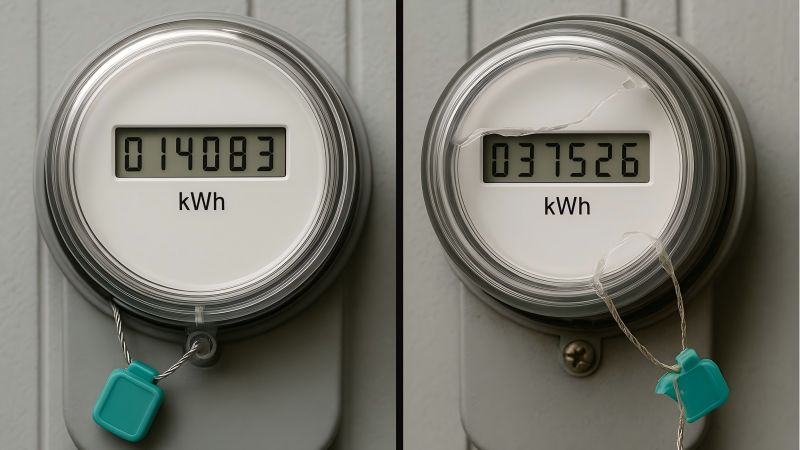
A seal "stops" fraud by making it irreversible. Its single-use design with a unique serial number means that once it is broken to tamper with a meter, it cannot be resealed or replaced without creating a permanent, visible, and documented discrepancy.
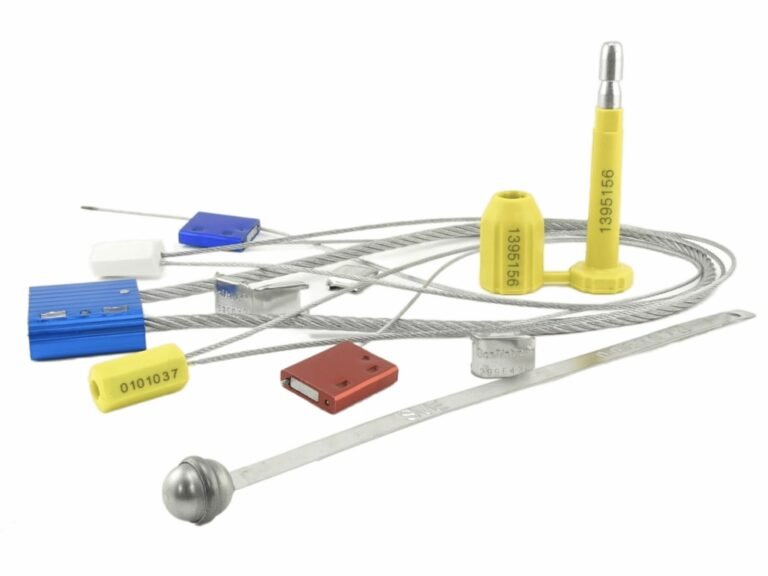
Let's be clear about the mechanics of this "intelligence-gathering device." Its physical design is not for resistance, but for communication. Its entire structure is a trap designed to be sprung by a single touch.
Single-Use Locking Mechanism
At the heart of every utility seal is a locking mechanism that is designed to be used only once. Whether it's a twist seal's metal insert or a padlock seal's clasp, once it clicks shut, the only way to open it is to destroy it. There is no key, no combination, no secret technique to open it non-destructively. This feature is the foundation of its evidentiary power.
The Power of the Serial Number
The true genius of the system is the unique serial number. This one feature transforms a simple piece of plastic into an auditable data point. When a technician applies a seal, they log Seal #12345 to Meter #ABCDE. If the next technician finds Seal #67890 or no seal at all, the information system flags an undeniable breach. A thief can break the plastic, but they cannot erase the number from your records. This turns a simple act of vandalism into a permanent, documented anomaly in your data trail.
Matching the Seal to the Threat: A Guide to Choosing the Right Protection?
Are you using the same generic seal for every single application, from residential meters to substation cabinets? This one-size-fits-all approach creates predictable vulnerabilities that sophisticated thieves can easily exploit.
Matching the seal to the specific threat vector is critical. Use wire-based twist seals for small meter apertures, robust padlock seals for hasps, and heavy-duty cable seals for high-risk infrastructure like transformers or substations.
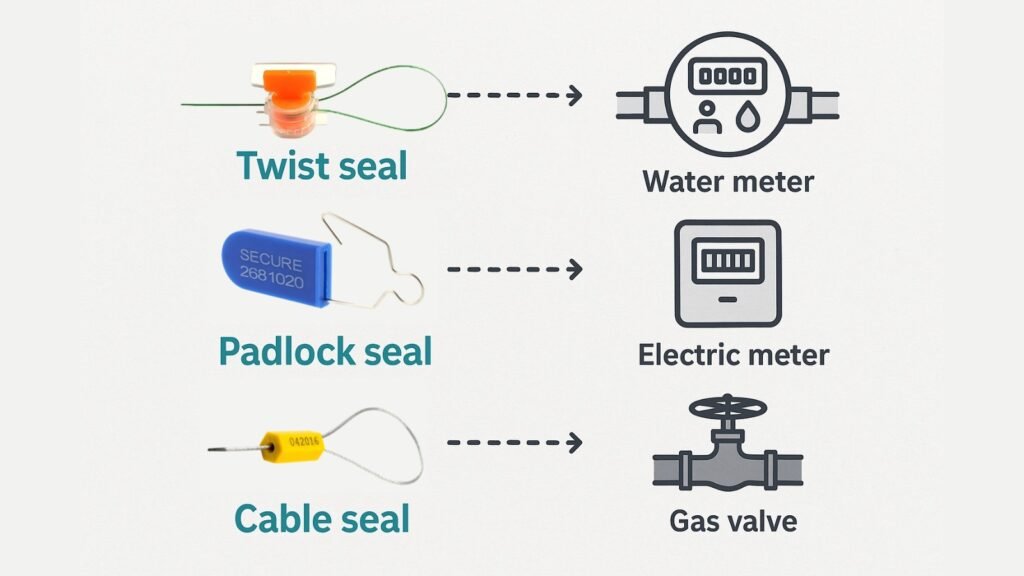
Deploying your "intelligence network" requires using the right sensor for the right location. Each seal type is a specialized tool designed to counter a specific method of attack or fit a specific piece of equipment perfectly.
| Seal Type | Best For | Strategic Function |
|---|---|---|
| Twist Seals | Standard residential/commercial meters with small locking holes. | The workhorse of your intelligence network. The thin wire can be adapted to various meter designs, ensuring a snug fit that's difficult to bypass without breaking. |
| Padlock Seals | Meter rings, cabinets, and boxes with hasp-style closures. | Provides a strong visual deterrent and is extremely fast to apply. Its solid body is more resistant to casual vandalism. |
| Cable Seals | Substation gates, transformers, high-value junction boxes. | A higher level of physical barrier. While still primarily for evidence, a steel cable seal requires tools to remove, adding a layer of delay and deterrence for more critical assets. |
From Sealing a Meter to Securing a Network: Building Your Auditing Protocol?
Do you think the job is done once the seal is applied? Without a rock-solid auditing protocol, your "intelligence network" is collecting data that no one is listening to, rendering it completely useless.
The seal is only the endpoint; the power is in the auditing protocol. This is the human and digital system that records, tracks, and—most importantly—flags discrepancies in your seal data. This is what turns data points into actionable intelligence.

This is where the psychological battle is won or lost. A thief who knows you have a weak or non-existent auditing process does not fear the seal. A thief who knows you have a rigorous, data-driven protocol sees the seal as an unbeatable witness. A truly effective protocol must include:
- A Centralized Seal Log: Whether it's a spreadsheet or a sophisticated software system, you need one central database that tracks the status of every single seal by its serial number and its assigned location.
- Mandatory Field Reporting: Every technician visit must include a check of the seal's integrity and a verification of its number against the log. "Seal OK, #12345" should be a required field in every service report.
- Automated Anomaly Flagging: Your system should automatically create an alert when a seal number is reported that doesn't match the master log. This discrepancy is the signal of a potential breach and must trigger an immediate investigation. This is your network's alarm bell.
- Chain of Custody for Seals: Unused seals must be treated as controlled items. Their serial numbers should be logged and assigned to specific technicians to prevent them from being stolen and used to conceal tampering.
Beyond Revenue Protection: Safeguarding Technicians and Public Safety?
Is your focus on electricity theft causing you to overlook an even greater risk? A tampered meter isn't just a financial problem; it's a ticking time bomb that poses a mortal threat to your employees and the public.
A broken or bypassed seal is a clear warning that an unqualified individual has dangerously modified high-voltage equipment. This creates a severe risk of electrocution for technicians and a significant fire hazard for the public.

When we discuss the "intelligence" gathered by our seal network, the most critical piece of information it provides is a safety warning.
- Protecting Technicians: When a service technician arrives at a location and the seal log shows a discrepancy, your protocol should treat this as a high-risk situation. The meter is no longer a standard piece of equipment; it is a potentially lethal, unknown variable. The technician can then take extra precautions, such as using insulated tools and personal protective equipment (PPE), assuming the internal wiring is unsafe.
- Preventing Public Catastrophe: Meter tampering often involves bypassing safety features like circuit breakers. This can lead to overloaded circuits, overheating wires, and ultimately, devastating fires. By identifying tampering early, your "intelligence network" is not just a revenue tool; it's a critical component of your public safety and fire prevention program.
What Are the Legal Consequences of Tampering with an Electric Meter?
How do you turn the evidence provided by a broken seal into a powerful legal deterrent? The seal's data is only as strong as the legal consequences it can trigger.
Tampering with an electric meter is a criminal offense in most jurisdictions, often classified as theft of services, criminal mischief, and trespassing. A broken seal provides the core, irrefutable evidence needed for successful prosecution, leading to hefty fines and even jail time.

This is the final move in the psychological war. The seal is your star witness. Utility companies work closely with law enforcement to build cases against perpetrators, and the meticulous data from your seal auditing protocol is the foundation of these cases. The legal process typically involves:
- Investigation: The documented seal discrepancy triggers an official investigation.
- Evidence Collection: The broken seal, photographs from the scene, and the meticulous seal log become the primary evidence.
- Prosecution: Charges are filed based on local and state laws. The clear, documented evidence of tampering makes these cases very difficult to defend against.
The public knowledge that your company not only detects but also prosecutes tampering is the ultimate deterrent. It changes the thief's calculation from a simple cost-benefit analysis to a serious risk of criminal conviction.
Conclusion
Stop fighting a physical battle. By deploying security seals as an intelligence network and backing them with a robust auditing protocol, you transform them into a powerful tool for deterrence, evidence gathering, and legal action.
Build Your Utility Intelligence Network Today
At ProtegoSeal, we provide the high-quality, uniquely serialized meter seals that form the foundation of a modern utility security strategy. We can help you choose the right tools for your intelligence network. Contact me to secure your revenue and public safety.