Are you lost in the confusing world of "tamper-proof," "tamper-resistant," and "tamper-evident"? Choosing the wrong strategy based on marketing hype can lead to a false sense of security and devastating financial losses.
These terms are not product tiers; they are three completely different security strategies. "Tamper-resistant" is a delaying tactic. "Tamper-evident" is an information tactic. And "tamper-proof" is a marketing myth you must avoid.

In my experience, the biggest mistake a buyer can make is to see these three terms as good, better, and best. They aren't. They represent three completely different security tactics, and a smart buyer must think like a commander choosing the right tactic for the right battlefield.
"Tamper-resistant" is a delay tactic, designed to slow an enemy down. "Tamper-evident" is an information tactic, designed to tell you exactly where the enemy has been. And "tamper-proof"? That's a dangerous marketing trap promising a battle that can't be won. Your job is to pick the right tactic for your mission.
Does "Tamper-Proof" Actually Exist? Debunking a Common Industry Myth?
Are you searching for a truly "tamper-proof" solution to guarantee 100% protection? Chasing this impossible ideal is a waste of time and money, and it distracts you from implementing security that actually works.
"Tamper-proof" does not exist. It's a marketing term, not a technical reality. Given enough time, resources, and determination, any physical security measure can be defeated. Believing in this myth is a critical strategic error.

As a strategic advisor, the first thing I do is remove the phrase "tamper-proof" from my clients' vocabulary. It sets a dangerous and unrealistic expectation. It suggests a magical, unbreakable shield. In the real world of logistics and security, there are no magical shields. There are only tools, tactics, and time. Even a bank vault, a symbol of impenetrability, can be breached by a skilled team with the right equipment. The goal of a professional security plan is not to achieve an impossible state of being "proof," but to implement a smart system that manages risk effectively. Any supplier who promises you a "tamper-proof" product is selling you a fantasy. A savvy commander ignores these siren songs and focuses on the real, effective tactics available.
What Does "Tamper-Resistant" Really Mean? The Strategy of Delay?
Do you believe a tamper-resistant device is meant to be an unbreakable wall? Its true purpose is far more strategic: it's not designed to stop an attack indefinitely, but to make it too slow and difficult to be worthwhile.
Tamper-resistance is a delay tactic. Its goal is to increase the time and effort required to breach a barrier so significantly that a thief is either deterred, gives up, or is caught in the act.

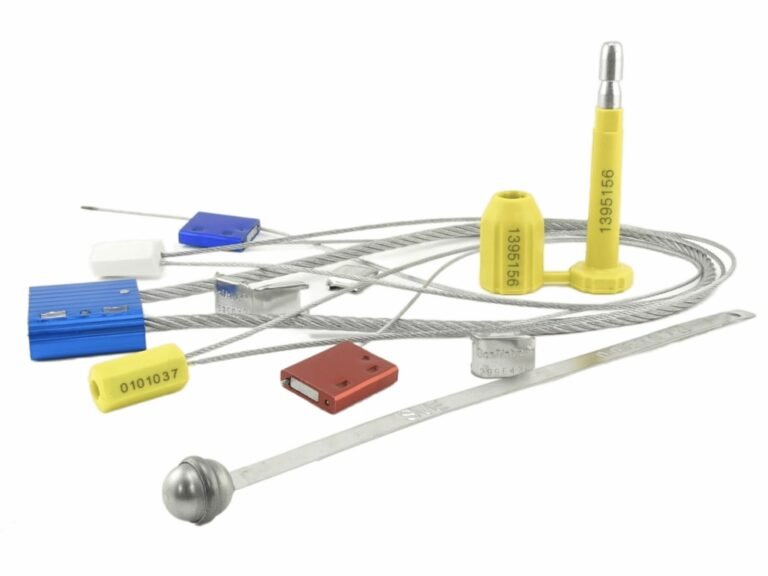
Think of this as defending a fortress. Your walls might not be indestructible, but they are thick enough to force the enemy to bring in heavy siege equipment, making a huge racket and taking a lot of time. In the security world, this is the role of tamper-resistant products. A high-security bolt seal made of hardened steel is a prime example. Can it be cut? Yes, with 40-inch bolt cutters and a lot of effort. A simple padlock on a medicine bottle cap is another example. The goal is to make access difficult enough that it slows down a potential adversary. This tactic is most effective in environments where there is a chance of surveillance or discovery. The longer the thief has to work, the greater their risk of being caught. It's security through engineered difficulty.
How Do "Tamper-Evident" Solutions Work? The Strategy of Information?
Think the only way to secure something is with a heavy lock? This overlooks a more subtle and often more powerful strategy that uses data, not just force, to protect your assets.
Tamper-evident solutions are an information tactic. They are not designed to stop an intruder, but to leave behind a clear, undeniable, and permanent record that an intrusion occurred. Their power lies in evidence, not resistance.

This is the intelligence branch of your security operation. The goal here isn't to fight the enemy at the gate, but to track their every move and report it back to headquarters. A uniquely numbered plastic seal is a perfect example. A thief can snap it off in a second. But they cannot replace it with another seal bearing the exact same serial number. This creates an unbreakable chain of information.
When the shipment arrives, if the number doesn't match the manifest, you have irrefutable proof of tampering. Security labels that leave a "VOID" message, or special bags that tear in a specific way, are other weapons in this information war. This tactic provides certainty and accountability. It might not stop the first theft, but the evidence it provides will absolutely stop the second.
Cost vs. Goal vs. Application: A Clear Comparison for B2B Buyers?
Are you struggling to decide which strategy is right for your shipment? Applying the wrong tactic to a situation is like sending a spy on a mission that requires a soldier—it's inefficient and likely to fail.

To help my clients choose, I always map out the options in a simple grid. It removes the confusion and makes the decision-making process logical and clear. The "battlefield" (your application) and the "mission objective" (your immediate goal) will dictate your choice of tactic. A mismatch is costly. Using a tamper-resistant bolt seal on an internal first-aid kit is expensive overkill. Using a simple tamper-evident seal on a cross-border shipment of diamonds is gross negligence. This table clarifies the choice.
| Tactic | Primary Goal (The Mission) | Method (The Weapon) | Ideal Scenario (The Battlefield) |
|---|---|---|---|
| Tamper-Resistant | Delay & Deter: Make entry slow, loud, and difficult. | Physical Hardness: Thick steel, complex locks, reinforced casings. | High-value cargo in semi-public areas where time is a risk factor. (e.g., truck trailers at a rest stop). |
| Tamper-Evident | Inform & Record: Provide undeniable proof of entry. | Uniqueness & Irreversibility: Serial numbers, void layers, special inks. | Assuring chain of custody and integrity. (e.g., evidence bags, pharma packaging, internal logistics). |
| "Tamper-Proof" | Marketing Claim: Offer a false promise of invincibility. | Buzzwords and hype. | Never a real option. A trap for inexperienced buyers. |
So, Which Type of Security Should You Choose for Your Business?
Feeling pressured to pick just one strategy for your entire company? The smartest commanders don't rely on a single tactic; they use a combined-arms approach, deploying different strategies for different situations.
The best approach is a layered one. Use tamper-resistant solutions to protect your high-risk perimeters and tamper-evident solutions to monitor the integrity of assets within those perimeters, creating an intelligent, multi-faceted defense.

Here is how you apply these tactics in the real world. For a high-value international shipment, your strategy should be:
- Deploy the Delay Tactic (Tamper-Resistant): Secure the container doors with a high-security, ISO 17712 compliant bolt seal. This is your "fortress wall."
- Deploy the Information Tactic (Tamper-Evident): Inside the container, seal the individual cartons or pallets with uniquely numbered security tape. This is your "internal surveillance system."
This combined approach gives you the best of both worlds. The bolt seal makes it hard for thieves to get in, and the tape tells you exactly where they went if they do. For lower-risk internal logistics, like totes moving between departments, the information tactic alone (a simple plastic seal) is perfectly sufficient. As the commander, you must assess the threat and deploy your forces accordingly.
Conclusion
Stop seeking a mythical "tamper-proof" product. Instead, think like a commander. Deploy the delay tactic of tamper-resistance for high-risk barriers and the information tactic of tamper-evidence for verifiable integrity.
We Are Your Strategic Security Partner
At ProtegoSeal, we don't just sell products; we provide the tools for your chosen security tactics. Whether you need to delay or inform, we have the solution. Contact me to design the right layered strategy for your business.